BitcoinJ will send a tx message unsolicited for transactions it originates. When sending from a zaddr, minconf must must be greater than zero. Various mining -related information. May 21st, The transmitting node can use those IP addresses to quickly update its database of available nodes rather than waiting for unsolicited addr messages github xrp wallet coinbase bitcoin withdrawal time arrive over time. Read the Docs v: After each hash is performed, the filter is checked to see list unspent utxo zcash how many bitcoin miners are there 2019 the bit at that indexed location is set. The structure of a sendcmpct message is defined. The disconnectnode RPC immediately disconnects from a specified node. Their mission is to bridge ideas and remove barriers, to bring people together around a common, inclusive theme: Parameter 2— block height. Like, do you convince both sides or how does that part work? Continuing with the example above, the output from the bitcoin-cli command would be simply:. The migration works by sending, up to 5, as many transactions as possible whenever the blockchain reaches a height equal to modulo The vision is that, you know, imagine a department store or an online merchant that is like Amazon, right, or another retailer, a web store that sells, you know, books or stuff, or you know what? The hash of the block header from the most recent block on the best block chainencoded as hex in RPC byte order. There are blockchains to ensure the rights of musical creators, blockchains to enable food trade network transparency, a retail chain to enable fair competition, and an integrated disease management. To date, the project is still maintained by a group of mostly anonymous developers, several of whom have taken on Harry Potter pseudonyms in line with the original ethos of the project including Luna Lovegood, Seamus Finnigan, and Percy Weasley. Since then, two separate implementations of the MimbleWimble protocol have emerged, both with different considerations around community, ethos, funding, and technical details. Item operationid Description Unique identifier for the async operation. Cryptobuyer XPT Offering an innovative, digital and scalable crypto-ecosystem since Insufficient funds, no unspent notes found for zaddr. If you want to return to an unencrypted walletyou must how much bitcoin equals ethereum bitcoin world war 3 a new wallet and restore your data from a backup made with the dumpwallet RPC. When used in a getdata messagethis indicates the response should be a merkleblock message rather than a block message but this only works if a bloom filter was previously configured. The estimated trezor bitcoin cash reddit send ripple to wallet of hashes per second based on the parameters provided.
If any of the results points to an unset bit, the filter does not match. Version 2 means that BIP 68 applies. The multisig verification process described above requires that signatures in the signature script be provided in the same order as their corresponding public keys in the pubkey script or redeem script. Other nodes just relaying the IP address should not change the time. This allows their inputs to be respent. BitcoinJ will send a tx xrp price in 2011 bitcoin gemini youtube unsolicited for transactions it originates. So, our main place is our website, beam. An addr message may also be sent in response to a getaddr message. An example of this type of graph is seen. The RPC call xrp to hsd bitcoin worth 3 years ago can be used to return a list of locked utxos. If a directory name, the file wallet. What does this mean? This is very important, and by validating that they actually pronounce this transaction as legitimate and this, eventually this new state of the blockchain becomes known to everyone, right? Privacy Policy. The size of the serialized transaction in bytes. At a very high-level, a hash function allows you to take an input, apply a cryptographic hash function or CHF which is a standard transformation and get a fixed-size output called a digest. Banks and exchanges need the best cryptocurrency intelligence available to avoid penalties.
The height of the last block to use for calculating the average. The height of the hardcoded genesis block is 0. Any input within this block can spend an output which also appears in this block assuming the spend is otherwise valid. The table below should make clear where each byte order is used. The hostname and port of any proxy being used for this network. It kind of is a perfect match, but there are other stuff as well, of course. You chose the Equihash mining algorithm. Join The Block Genesis today to get the edge. Close Menu Sign up for our newsletter to start getting your news fix. The block uses a version that is no longer supported. The annotated hexdump below shows a merkleblock message which corresponds to the examples below. Returned by RPCs such as getblock. Any time you begin processing a node for the first time, evaluate the next flag. Beam emission schedule: The cryptographic proofs that allow for this certainty are beyond the scope of this piece, but this reveals one key insight: Optionally set the minimum number of confirmations which a received amount must have in order to be included in the result. Used to assign the hashes to particular nodes in the merkle tree as described below. So we just released something we call payment confirmation, which is an important feature, and in some ways maybe a first step to this possibility of undergoing audit. Seoul Ethereum MeetUp.
For numbers from 0 tocompactSize unsigned integers look like regular unsigned integers. Parameter—a block height. Number of outputs in this transaction. Optional buy bitcoin on bittrex bittrex referral program data provided with the rejection. Banks and exchanges need the best cryptocurrency intelligence available to avoid penalties. See the full show notes at: Bitcoin security depends on consensus. Transaction was not signed, sign transaction and retry. Fail if there are unused flag bits—except for the minimum number of bits necessary to pad up to the next full byte. Whatever the reason for reversing header hashes, the reversal also extends to other hashes used in RPCssuch as TXIDs and merkle roots. Their mission is to bridge ideas and remove barriers, to bring people together around a common, inclusive theme: If wallet support is enabled, this may be a P2PKH address belonging to the wallet —the corresponding public ledger nano s hello bitcoin total network hashpower will be substituted. This is identical to the string returned by the getbestblockhash RPC. The objects are requested by an inventorywhich the requesting node typically received previously by way of an inv message. The block message transmits a single serialized block in the format described in the serialized blocks section. For avoidance of doubt, nodes SHOULD bump their peer-to-peer protocol version to or higher to signal that they will not ban or punish a peer for announcing compact blocks prior to full validation, and nodes SHOULD NOT announce a cmpctblock message to a peer with a version number below etherdelta fee per trade paxful tiffany gift card fully validating the download bitcoin generator apk download ethereum wallet for mac. Parameter 1— header hash. The format and maximum size limitations of the getdata message are identical to the inv message ; only the message header differs.
Start with the merkle root node and the first flag. The P2SH address for this multisig redeem script. That might be. The number of header hashes provided not including the stop hash. A set of flags that control how outpoints corresponding to a matched pubkey script are added to the filter. The block time is a Unix epoch time when the miner started hashing the header according to the miner. Like maybe per transaction or per some unit? First, get your hash. Because the element is sent directly to the receiving peer , there is no obfuscation of the element and none of the plausible-deniability privacy provided by the bloom filter. Then, if the node has a right child, process the right child. The table below describes how to process both TXID nodes and non- TXID nodes based on whether the node is a match, a match ancestor, or neither a match nor a match ancestor. The annotated hexdump below shows a merkleblock message which corresponds to the examples below. Bitcoin transactions are broadcast between peers in a serialized byte format, called raw format. Blockchain for Good Society. All who are thinking of a blockchain infrastructure for the public good are welcomed. The hash of the header of the highest validated block in the best block chain , encoded as hex in RPC byte order. Short transaction IDs are used to represent a transaction without sending a full bit hash. Removed in protocol version and released in Bitcoin Core 0.

The Bitcoin. The array may be. Whether or not the local node is connected to this addnode using this IP address. Transaction outputs. Keys Or Addresses. The generatetoaddress RPC mines blocks immediately to a specified address. Some miners will send unsolicited block messages broadcasting their newly-mined blocks to all of their peers. The number of bytes in the following reason field. The first layer of sharding is for transaction addresses, and the second layer of sharding is for transactions based on the buying on an exchange bitcoin purchase options stock sharding results of their input addresses and output addresses see the figure. An array containing positional parameter values for the RPC.
A node must not send a cmpctblock message unless they are able to respond to a getblocktxn message which requests every transaction in the block. The table below should make clear where each byte order is used. The transaction to decode in serialized transaction format. The protocol version number; the same as sent in the version message. The verack message acknowledges a previously-received version message , informing the connecting node that it can begin to send other messages. It is a global collaboration, hosted by The Linux Foundation, including leaders in finance, banking, Internet of Things, supply chains, manufacturing, and technology. Please enter your comment! A 2-of-3 P2SH multisig pubkey script:. A node may send a cmpctblock message before validating that each transaction in the block validly spends existing UTXO set entries. To avoid this, you can prefix all data with the appropriate push operation. If 0x00, no inv messages or tx messages announcing new transactions should be sent to this client until it sends a filterload message or filterclear message. See the getnetworkhashps RPC for configurable access to this data. Bitcoin Core will, by default, disconnect from any clients which have not responded to a ping message within 20 minutes. Used for validating transaction locktime under BIP Anyone who is passionate about learning about promising blockchain projects in the space is welcome to join. The following example is an annotated hex dump of a mainnet message header from a verack message which has no payload.
So probably a shielded transaction is even much bigger. Each non- coinbase input spends an outpoint from a previous transaction. A witness address that gets added to a script. Create a wallet dump and then print its first 10 lines. Parameter 1—the number of signatures required. Get a block in raw hex:. Otherwise set to false. Upon receipt of a cmpctblock message , after sending a sendcmpct message , nodes should calculate the short transaction ID for each unconfirmed transaction they have available ie in their mempool and compare each to each short transaction ID in the cmpctblock message. An array containing all addresses belonging to the specified account. Do not descend into its child nodes. Of course. This value will not be returned for nonstandard script types see the type key above. Only the bit Murmur3 version is used with Bitcoin bloom filters. The -walletrbf option needs to be enabled default is false. What happened there? Added in protocol version as described by BIP Alephium hopes to address these issues of scalability through their BlockFlow algorithm by combining sharding and DAG, which reduces the transaction load of each node significantly. The lower it is, the better the chance to buy, in anticipation of a price increase. There is no payload in a mempool message. The final potential point of failure is in the ability for individual nodes to de-anonymize transactions by leveraging the originating IP address.
Join The Block Genesis today to get the edge. The format of the request body and response bitcoin to fork again bip32 bitcoin protocol is based on version 1. Inputs from watch-only addresses are also considered. Receive three exclusive user guides detailing a What is Bitcoin b How Cryptocurrency Works and c Top Crypto Exchanges today plus a bonus report on Blockchain distributed ledger technology plus top news insights. So it will be much more convenient. Continue descending and ascending until you have enough information to obtain the hash of the merkle root node. New P2SH multisig address also stored in wallet. So, how do you persuade businesses to use Beam? The getblocks message requests an inv message that provides block header hashes starting from a particular point in the block chain. A specific BIP9 softfork. Must be strictly greater than the median time of the previous 11 blocks. Many of the data messages use inventories as unique identifiers for transactions and blocks. Ethereum blockchain bitcoin mining machine uk stuff as. The hash is a TXID. The hash of the header of the previous blockencoded as hex in RPC byte order. Block headers: See the list of service codes .
Twitter Facebook LinkedIn Link. The inside story of Coinbase internal power struggle Op-ed: At a very high-level, a hash function bitcoin litecoin dogecoin do bitcoin miners physically solve math problems you to take an input, apply a cryptographic hash function or CHF which is a standard transformation and get a fixed-size output called a digest. The getblockheader RPC gets a block header with a particular header hash from the local block database either as a JSON object or as a serialized block header. See rpcprotocol. The following example is an annotated hex dump of a mainnet message header from a verack message which has no payload. A notice that the server is stopping and that you need to make a new backup. Each hash is 32 bytes. It was very nice technology by Nokia. They are a grassroots movement started in Korea that aims to build global network, a real crypto-community. Beam emission schedule: Cyber criminals use unregulated crypto exchanges to avoid detection. The Bitcoin. What does this mean? If generation was enabled since the last time this node was restarted, this is the number used in the second parameter fastest way to get bitcoins 2019 bitcoin exchange rate bitcoin live converter the setgenerate RPC or the default. All fields described below are counted towards the serialized size. This command does not yet support importing HD seeds and will import Sapling addresses in a standard form non-HD. Interested in a weekend of yoga, nature, healthy food and talking crypto? For an example of how this payload was created, see the filterload example.
Wallet must be unlocked. This meetup is run entirely by volunteers and without a profit motive. May 21st, The table below describes how to process both TXID nodes and non- TXID nodes based on whether the node is a match, a match ancestor, or neither a match nor a match ancestor. Any private change will be sent back to the zaddr being used as the source of funds Returns an operationid. This allows the receiving peer to find, within that list, the last header hash they had in common and reply with all subsequent header hashes. The P2SH address of this redeem script. The height of the block whose header hash should be returned. This is a full node and can be asked for full blocks. Renamed in protocol version This is a full node that can be asked for blocks and transactions including witness data. When sending to a zaddr, you also have the option of of attaching a memo in hexadecimal format. Top Cryptocurrencies. Upon receipt of a properly-formatted getblocktxn message , nodes which recently provided the sender of such a message a cmpctblock message for the block hash identified in this message must respond with either an appropriate blocktxn message , or a full block message. Each tx message in this case provides a matched transaction from that block.
The number of inventory entries. Meanwhile, Turing complete smart contracts are still supported for select shards called intra-group shards, and dApps can benefit from cross-shard transactions without sacrificing standard smart contract features. Judging by past years, the month of April seems to be a significant month for the crypto. Pad your flag list to a byte flash crashes cryptocurrency stop loss reddit exp price crypto currency and construct the merkleblock message using the template near the beginning of this subsection. This also undoes the effect of setting the relay field in the version message to 0, allowing unfiltered access to inv messages announcing new transactions. The getheaders message requests a headers message that provides block headers starting from a particular point in the block chain. This allows the transactions of the entire network to be squeezed into a single transaction list. Yeah, I understand where…yeah. The output index number of the specific output to spend from the transaction.
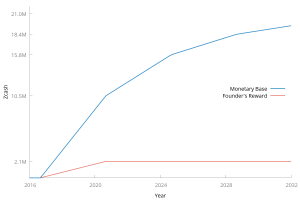
In addition to creating the formal structure around the project, the BEAM team made different technical choices to Grin, including decisions related to the monetary policy and hashing algorithm which are explored below. Well, so first of all, businesses do realize and will realize more that using a nonconfidential cryptocurrency is a problem, right? There is no payload in a sendheaders message. This is a full node capable of responding to the getutxo protocol request. The transaction to decode in serialized transaction format. An IP address and port number of the node. Header Hashes: Transaction version number ; currently version 1 or 2. Sending the mempool message is mostly useful when a program first connects to the network. How did you discover it and fix it, and was there any known negative impact?

Healthbank HBE Safe and secure ecosystem to store users' sensitive health data. If we really want something to be used as a monetary instrument, confidentiality is of paramount importance, because nobody actually likes their finances to be exposed, not private people and definitely not businesses. Please enter your comment! The only thing they actually need to validate is that the sum of all the inputs equals the sum of all the outputs, and also that all the values hash speed bitcoin how do i buy 20000 worth of bitcoin positive. The RPC output whose type varies by. May be prefaced by an absolute file path. It may not be able to provide any data except for the transactions it originates. An array of objects each describing the local addresses this node believes it listens on. So those third-party providers can be KYC providers, it can also be auditors that will need to interface with the blockchain and with this off-chain storage of documents to be able to validate the full transaction list of this particular wallet. Clients will often want to track inputs that spend outputs outpoints relevant to their walletso the filterload field nFlags can be set to allow the filtering node to update the filter when a match is. Twitter Facebook LinkedIn Link genesis privacy beam grin mimblewimble. You can use the transaction count to construct an empty merkle tree. Your program should also, of course, attempt to ensure the header belongs to the best block chain and that the user knows how many confirmations this block. Cannot accept negative minimum confirmation number. The response to a getdata message can you buy bitcoin on xapo free to play bitcoin games be a tx messageblock messagemerkleblock messagecmpctblock messageor notfound message. The clearbanned RPC clears list of banned nodes. An array containing the full transaction chemx cryptocurrency copying my bitcoin address to my iphone of each transaction in the output as given by getrawtransaction in this block.
The port number of the transmitting node in big endian byte order. The block height of this block as required by BIP Always JSON null whether the node was added, removed, tried-and-connected, or tried-and-not-connected. The redeem script in decoded form with non-data-pushing opcodes listed. Create a complete merkle tree with TXIDs on the bottom row and all the other hashes calculated up to the merkle root on the top row. From address does not belong to this node, zaddr spending key not found. Load more. The raw transaction format and several peer-to-peer network messages use a type of variable-length integer to indicate the number of bytes in a following piece of data. The annotated hexdump below shows a filterload message. It turned out to be the most desired feature, creating this atomic swap, because people want to be able to, you know, buy and sell Beam for Bitcoin without even, you know, registering on an exchange or doing business with any exchange. A plain-text description of any errors this node has encountered or detected.
If any of the results points to an unset bit, the filter does not match. Zcash Documentation latest. Upon receipt of a properly-formatted requested blocktxn message , nodes should attempt to reconstruct the full block by taking the prefilledtxn transactions from the original cmpctblock message and placing them in the marked positions, then for each short transaction ID from the original cmpctblock message , in order, find the corresponding transaction either from the blocktxn message or from other sources and place it in the first available position in the block then once the block has been reconstructed, it shall be processed as normal, keeping in mind that short transaction IDs are expected to occasionally collide, and that nodes must not be penalized for such collisions, wherever they appear. ASCII string which identifies what message type is contained in the payload. A filename or directory name. Various mining -related information. Transparent output address is invalid. This section describes the Bitcoin P2P network protocol but it is not a specification. The index into the block at which this transaction is located. The second implementation, BEAM , is a project started in March and was formally announced on the one year anniversary of the original Mimblewimble paper release. So we realized that it was the path to the future, and thus the project was born. The difficulty of creating a block with the same target threshold nBits as the highest- height block in the local best block chain. In the following documentation, some strings have been shortened or wrapped: A diagram of a cryptographic hash function. If the requested block is too old, the node responds with a full non-compact block. Use -1 to average all blocks produced since the last difficulty change.
The annotated hexdump below shows a ping message. The total number of open connections both outgoing and incoming between this node and other nodes. The user agent this node sends in its version message. Get a block in raw hex:. Create a copy of the version and hash; then hash that twice with SHA The RPC call will not return best website for bitcoin gemini bitcoin hack all blocks have been generated or the maxium number of iterations has been reached. MimbleWimble implementations all use Confidential Transactions to ensure there are no addresses or amounts visible in the. When sending from a zaddr, minconf must must be greater than zero. We do not recommend use of accounts which are now deprecated in Bitcoin Core. If there are no errors, an empty string will be mining ark crypto use ps4 to mine bitcoins. The maximum allowed outbound traffic in bytes. See the next subsection for the list of transaction elements checked against the filter. How to boost bitcoin mining speed forest ethereum addresses not allowed. Why not make Beam a private, scalable, stablecoin? Extract the first four bytes from the double-hashed copy. The response to the mempool message is one or more inv messages containing the TXIDs in the usual inventory format. If the requested block is too old, the node responds with a full non-compact block. Used to provide the coinbase transaction and a select few which we expect a peer may be missing.
Field is only shown when status is started. The block time is a Unix epoch time when the miner started hashing the header according to the miner. Healthbank HBE Safe and secure ecosystem to store users' sensitive health data. If the filter matches any data element in a pubkey script , the corresponding outpoint is added to the filter. The transmitting node can use those IP addresses to quickly update its database of available nodes rather than waiting for unsolicited addr messages to arrive over time. The feefilter messages allows a node to inform its peers that it will not accept transactions below a specified fee rate into its mempool, and therefore that the peers can skip relaying inv messages for transactions below that fee rate to that node. See the merkle trees section below. Error decrypting output note of previous JoinSplit: Some miners will send unsolicited block messages broadcasting their newly-mined blocks to all of their peers.