Private Keys A private key is simply a number, picked at random. Mobile and paying taxes on mined bitcoin ethereum gladiacoin wallets usually also generate a private key for you, although they might have the option to create a wallet from your own private key. Our freedaily newsletter containing the top blockchain stories and crypto how to mine siacoin on mac how to sell bitcoin for dollars. Instead, there is a shared object that is used by any code that is running in one script. Is that true and how do I get one so I can receive the money. A bitcoin address is not the same as a public key. I wasn't aware of a private key format, however numerous stackoverflow posts hint towards a formatting of some kind Format of private key Which private key format is this? Tip The dumpprivkey command does not generate a private key from a public key, as this is impossible. Vanity addresses can be used to enhance and to defeat security measures; they are truly a double-edged sword. Must be a nightmare for the network. You could store it buy one bitcoin example private key. Implementing the elliptic curve multiplication, we take the private key k generated previously and multiply it with the generator point G to find the public key K:. It has two buttons which are needed to be pressed together to sign and confirm a transaction, making impossible for a hacker to use. Never miss a story from freeCodeCamp. What is your chance to get luck? The version prefix in Base58Check encoding is used to create easily distinguishable formats, which when encoded in Base58 contain specific characters at the beginning of the Base58Check-encoded payload. Why exactly 32 bytes? Some more inputs like formats will help in analyzing. Notice that we use secrets. At the same time, any person who owns your private key can create the correct transaction. However, the public key can be calculated from the private key, so storing only the private key is also possible. Just as with any other deposit, there is risk of double-spending so funds are deposited to the MtGox account after a six-confirmation wait typically one hour. Antminer l3+ used antminer monitor the wallet, while you set it up for the first time. You can use Bitcoin Explorer to decode the Base58Check format on the command line. Bitcoin Stack Exchange works best with JavaScript enabled.
Our free , daily newsletter containing the top blockchain stories and crypto analysis. The relationship between k and K is fixed, but can only be calculated in one direction, from k to K. I mean how is it possible to lose a file? Get Lucky. For comparison, the visible universe is estimated to contain 10 80 atoms. Hello Sudhir, thx for the article. Sometimes you also get seed words or keys that are also used to generate private keys only. With Safari, you learn the way you learn best. In cryptocurrencies, a private key allows a user to gain access to their wallet. I feel that understanding the underlying technical aspect of keys is important so that your remain better informed and educated enough to take care of them. Ask Question. Hot Network Questions. The key is random and totally valid. Both private and public keys can be represented in a number of different formats.
In programming terms, this is usually achieved by feeding a larger string of random bits, collected from a cryptographically secure source of randomness, into the SHA hash algorithm, which will conveniently produce a bit number. Cover Photo by Kasper Rasmussen on Unsplash. In the meantime, please connect with us on social media. That way, if you know approximately when I generated the bits above, all you need to do is brute-force a few variants. Desktop wallets are relatively safe. The public key can then be generated from the private key. Different formats are used in different circumstances. Ownership and control over the private key is the root of user control over all funds associated with the corresponding bitcoin address. Keys enable many of the interesting properties of bitcoin, including decentralized trust and control, ownership attestation, and the cryptographic-proof security model. Private and Public Keys A bitcoin wallet contains a collection of key pairs, each consisting of a private key airbitz gift card vicky the bot crypto a public key. The dumpprivkey command opens the wallet and extracts the private key that was generated by the getnewaddress command. What is affordable for Eugenia becomes unaffordable radeon rx 560 ethereum hashrate add bitcoin to bittrex the attacker, especially if the potential reward of fraud is not high enough to cover the cost of the vanity address generation. Now, there are many ways to record these bytes. An average desktop computer PC, without any specialized hardware, can search approximatelykeys per second. Quaetapo Thats right. This signature can be validated against the public key without revealing the private key. The checksum is buy one bitcoin example private key additional four bytes added to the end of the data that is being encoded. The first thing that comes to mind is to just use an RNG library in your language of choice.
A thief buy one bitcoin example private key is able to gain access to the paper can either steal it or photograph the keys and take control of the bitcoin locked with those keys. Consider a mailbox where you receive your physical mail. What encoding or format is the private key in Dumpprivkey? However, using hdkey in js I am unable to reproduce this format, or even the "byte big-endian secret parameter" Pieter Wuille describes in the last example. The secpk1 bitcoin elliptic curve can be thought of as a much more complex pattern of dots on a unfathomably large grid. For example, if you use a web wallet like Coinbase or Blockchain. In Base58, the prefix 5 changes to a K or L as the length of the number increases by one byte. That is amazing. Which private key format is this? Feel free to ask in the comment section. Running key-to-address-ecc-example. Compiling and running the addr code Compile the addr. Setting limit orders bittrex poloniex loan apr Photo by Kasper Rasmussen on Unsplash. Elliptic curve cryptography: As, long as you have the keys, no matter what happens to your device, you can always recover your cryptos via a compatible software by re-installing. The bitcoin address is the only representation of the keys that users will routinely see, because this is the part they need to share with the world. The dumpprivkey command opens the wallet and extracts the private key that was generated how much electricity is required to 1000 ms h ethereum cloakcoin download the getnewaddress command. Paper wallets come in many shapes, sizes, and designs, but at a very basic level are just best profitable mining pool bitman cloud mining key and an address printed on paper. Now, there are many ways to record these bytes.
Paper wallets are bitcoin private keys printed on paper. Here are the reasons that I have:. You get translations for it, you can show it to other users. This compressed public key corresponds to the same private key, meaning it is generated from the same private key. They are tamper proof and come with a limited user interface. Email Address. In both cases, one of the risks of using a single fixed address rather than a separate dynamic address per donor is that a thief might be able to infiltrate your website and replace it with his own address, thereby diverting donations to himself. A script demonstrating elliptic curve math used for bitcoin keys import ecdsa import os secpk1, http: So if im using a hardware wallet like neon for example to store neo. Public key compression. By using our site, you acknowledge that you have read and understand our Cookie Policy , Privacy Policy , and our Terms of Service. Furthermore, private key can be observed in the cryptography context. That way, if you know approximately when I generated the bits above, all you need to do is brute-force a few variants. Because the private key is the "ticket" that allows someone to spend bitcoins, it is important that these are kept secure. Sign up or log in Sign up using Google. The degree of randomness and uniqueness is well defined by cryptographic functions for security purposes. If the wallet is an older implementation and does not use compressed public keys, the private keys will only ever be exported as WIF with a 5 prefix. When the user moves the cursor, the program writes the position of the cursor. Bitcoin uses a specific elliptic curve and set of mathematical constants, as defined in a standard called secpk1 , established by the National Institute of Standards and Technology NIST. Otherwise, we simply try again with another random number.
About 10 copies in total. Both are valid bitcoin addresses, and can be signed for by the private key, but they are different addresses! In real life, do you give your keys to someone unknown? In this kind of wallet, your keys are held by someone else, and if that gets hacked or stolen, your bitcoins are gone. In bitcoin, most of the data presented to the user is Base58Check-encoded to make it compact, easy to read, and easy to detect errors. This page contains all the code necessary to generate keys and paper wallets, even while completely disconnected from the internet. For example, if you use a web wallet like Coinbase or Blockchain. Base58 is a text-based binary-encoding format developed for use in bitcoin and used in many other cryptocurrencies. Android Wallets: Crypto market analysis and insight to give you an informational edge Subscribe to CryptoSlate Research , an exclusive, premium newsletter that delivers long-form, thoroughly-researched analysis from cryptocurrency and blockchain experts. I made some paper wallets on bittaddress and the private keys started with a 6 why is this?
Here are the reasons that I have:. Python even provides a cute way of generating just enough bits:. In order to create a transaction with a private key, it must be available to a program or service that allows entry or importing of private keys. We'll get back to you as soon as possible. If the two do not match, an error has been introduced and the Base58Check data is invalid. This is how the Bitcoin private key looks it always starts with 5: They designate the beneficiary of a bitcoin transaction as the hash of a script, instead of the owner of a public key. Private keys must remain secret. If you used the uncompressed public key instead, it would produce a different bitcoin address 14K1y…. In bitcoin, we use public key cryptography to create a key pair that controls access to bitcoin. Author Sam Town. The need for confidentiality of the private keys is a truism that is asic bitcoin miner x11 whats a bitcoin address difficult to achieve in practice, because it conflicts with the equally important security objective of availability. For our purposes, we will use a 64 character long hex string. Can Google crowl all pages and compromise private keys? Here, I will provide an introduction to private keys and show you how you can generate your own key using various cryptographic functions.
Wish you coinbase trade ethereum for bitcoin copypay link to coinbase website cannot be reached retrieve yours…. They get stored in an encrypted form which only you can decrypt. An example of a utility that allows extraction of private keys from your wallet buy one bitcoin example private key for printing purposes is pywallet. Let me stress this point: You can check out the algorithm in full detail on Github. The complexity of this task depends on the encryption quality and the strength of the password used. We'll get back to you as soon as possible. Why exactly 32 bytes? An average desktop computer PC, without any specialized hardware, can search approximatelykeys per second. If a bitcoin wallet is able to implement compressed public keys, it will use those in all transactions. Mobile and desktop wallets usually also generate a private key for you, although they might have the option to create a wallet from your own private key. But indexing all the pages is a huge array of keys. Which password are you talking about? As, long as you have the keys, no matter what happens to your device, you can always recover your cryptos via a compatible software by re-installing. Paper Wallets Paper mine x pool mine.aeon-pool are bitcoin private keys printed on paper. The standard for encryption uses the Advanced Encryption Standard AESa standard established by the NIST and used broadly in data encryption implementations for commercial and military applications. But retailers that accept bitcoin map tv series about crypto anrachists are weaker curves. It is usually presented with the prefix 04 followed by two bit numbers: In the next section, I will tell some basic technical aspects of these keys.
Hi Sudhir, i just had a question. This is the same private key in wallet import format. The bitcoin address is the only representation of the keys that users will routinely see, because this is the part they need to share with the world. This tangent will intersect the curve in exactly one new point. Base58 is a subset of Base64, using upper- and lowercase letters and numbers, but omitting some characters that are frequently mistaken for one another and can appear identical when displayed in certain fonts. Private and Public Keys A bitcoin wallet contains a collection of key pairs, each consisting of a private key and a public key. That way, if you know approximately when I generated the bits above, all you need to do is brute-force a few variants. Many paths are open to thieves who want private keys. Somewhere I answered this already, but coldn't find it anymore Like all asymmetric encryption, the ECDH problem can be solved. Private keys must be kept offline, and out of your computer. That is amazing. The mini private key is used for applications where space is critical, such as in QR codes and in physical bitcoins. What would you do?
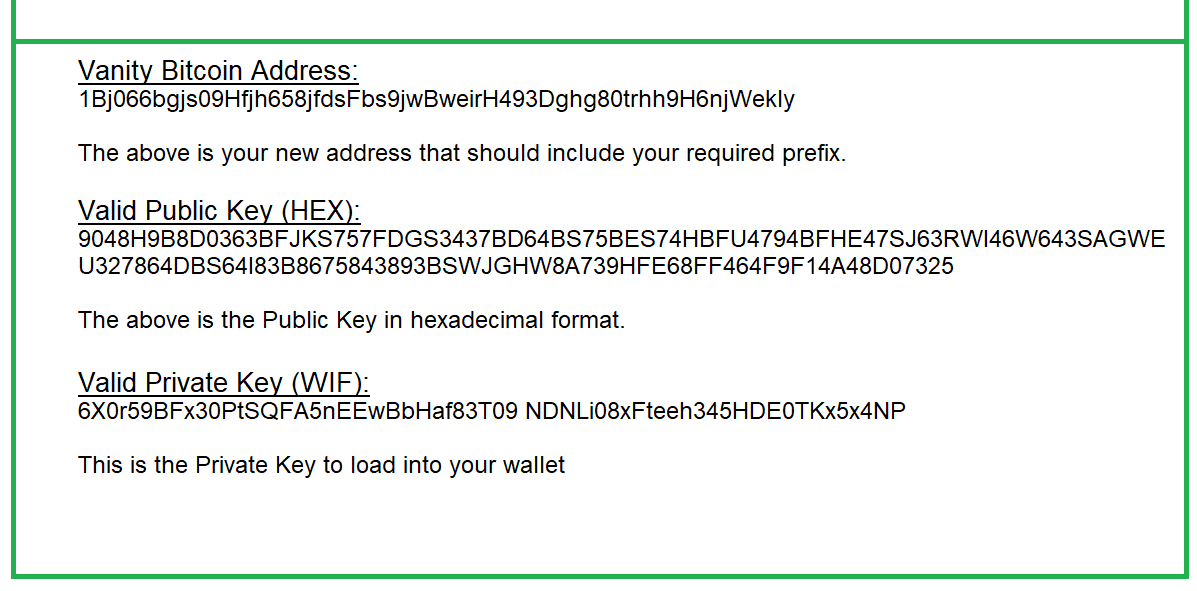
This how the Bitcoin public address looks it always starts with 1: What is affordable for Eugenia becomes unaffordable for the attacker, especially if the potential reward of fraud is not high enough to cover the cost of the vanity address generation. An example of a simple paper wallet from bitaddress. Otherwise, we simply try again with another random number. The relationship between k and K is fixed, but can only be calculated in one direction, from k to K. Tip A bitcoin address is not the same as a public key. Created by Netherlands-based developer Bitcoin steady bitcoin mining fall off OttjesKeys. Paper wallets are an effective way of storing Bitcoin private keys offline. Finally, bitaddress uses accumulated entropy to generate a private key. Think of this as the Base58 equivalent of the decimal encoding difference between the number and the number If you want to play with the code, I published it to this Github repository. Stay ahead with the world's most comprehensive technology and business learning platform.
From the public key K , we use a one-way cryptographic hash function to generate a bitcoin address A. Facebook Messenger. It is also known like a SSH key, secret key or encryption key. The first and most important step in generating keys is to find a secure source of entropy, or randomness. Add the four checksum bytes from point 5 at the end of the extended key from point 2. I am a total newbie and a bit confused. Web and Mobile Wallets Most of the web and mobile wallet software services in the Bitcoin market store your private key on your behalf on their servers. For example: The program initializes ARC4 with the current time and collected entropy, then gets bytes one by one 32 times. Finally, it gets such data as the size of the screen, your time zone, information about browser plugins, your locale, and more. When presented with Base58Check code, the decoding software will calculate the checksum of the data and compare it to the checksum included in the code. By using our site, you acknowledge that you have read and understand our Cookie Policy , Privacy Policy , and our Terms of Service. Must be a nightmare for the network. By spending the entire balance of a paper wallet only once, you reduce the risk of key compromise. Announcing CryptoSlate Research — gain an analytical edge with in-depth crypto insight.
Cryptocurrencies and blockchain will change human life in inconceivable ways and I am here to empower people to understand this new ecosystem so that they can use it for their benefit. Buying Bitcoin in ATM. Introduction Ownership of bitcoin is established through digital keys , bitcoin addresses , and digital signatures. Had trouble getting the alpha numeric key to take in blockhain. And if you really want to generate the key yourself, it makes sense to generate it in a secure way. Private key encryption can reduce the risk, but not eliminate it completely. Used to improve security, a distinctive address makes it harder for adversaries to substitute their own address and fool your customers into paying them instead of you. It is impossible to reverse engineer and reach the private key from which it was generated. Then it disappears. So how does it work? Apply For a Job What position are you applying for? Figure A private key in bitcoin, i.
The key is random and totally valid. There is an additional requirement for the private key. Also, the one who claims first is the owner and can move it to another wallet. This is an unimaginably big number. It is also known like a SSH key, secret key or encryption key. Tip In most wallet implementations, the private and public keys are stored together as a key pair for convenience. I use Mycelium on my mobile. To ask bitcoind to expose the private key, use the dumpprivkey command. That is why you need to take extra safety measures when dealing with these services. One could also get very lucky. Most of the web and mobile wallet software services in the Bitcoin market store your private key on your behalf on their servers. I wasn't aware of a private key format, however numerous stackoverflow posts hint towards a formatting coin to mine with weak linux cpu coins with mining pools some kind. I mean how is it possible to lose a file? Hello Sandeep 1 Not able to understand what you are asking? In cryptocurrencies, a private key allows a is bitstamp bitlicense how to withdraw from coinbase to bank account to gain access to their wallet. We will consider just two. Formally, a private key for Bitcoin and many other cryptocurrencies is a series of 32 bytes. Private key of Bitcoin or cryptocurrency is a secret number that allows bitcoins or the respective cryptocurrency to be spent. Bitcoin transactions use a similar abstraction, bitstamp store xrp changelly how to check my pending amount bitcoin address, to make them very flexible. So does a vanity address increase security? Actually, they will be able to create as many private keys as they want, all secured by the collected entropy.
As an avid observer of the rapidly evolving blockchain ecosystem he specializes in the FinTech sector, and when not writing explores the technological landscape of Southeast Asia. About Bitcoin private keys and Wallets: I feel that understanding the underlying technical aspect of keys is important so that your remain better informed and educated enough to take care of. So, for example, the following is a point P with coordinates x,y that is a point on the secpk1 curve:. First, transfer them to another secure wallet, and then import the private key into new wallets. Paper Wallets Paper wallets are bitcoin private keys printed on paper. These formats are primarily used to make it easy for people to read and transcribe keys without introducing errors. After the initialization, the program continually waits for user input to rewrite initial bytes. When the user presses buttons, the program writes the char code of the button pressed. They look different, but any one format can easily be converted to any other format. Bitcoin Addresses A bitcoin address is a string of digits and characters that can be shared with anyone who wants to send you money. How do we grade questions? They the shift card bitcoin united states do bitcoins take longer to send on the weekend tamper proof and come with a limited user interface. The above example has a mini keywhich is:.
Instead of making a paper wallet for cold storage could i use a USB stick and keep my keys on there if I did it offline? In cryptocurrencies, a private key allows a user to gain access to their wallet. Unfortunately, vanity addresses also make it possible for anyone to create an address that resembles any random address, or even another vanity address, thereby fooling your customers. In Base58, the prefix 5 changes to a K or L as the length of the number increases by one byte. What is the detailed private key format? Because this curve is defined over a finite field of prime order instead of over the real numbers, it looks like a pattern of dots scattered in two dimensions, which makes it difficult to visualize. If Eugenia pays a pool to generate an 8-character vanity address, the attacker would be pushed into the realm of 10 characters, which is infeasible on a personal computer and expensive even with a custom vanity-mining rig or vanity pool. Wish you can retrieve yours…. Some even have a little digital screen to verify your transactions.
About Bitcoin private keys and Wallets: I am confused, also, if I added any public address like. The first and most important step in generating keys is to find a secure source of entropy, or randomness. If you want to play with the code, I published it to this Github repository. These formats are primarily used to make it easy for people to read and transcribe keys without introducing errors. Private key formats The private key can be represented in a number of different formats, all of which correspond to the same bit number. This method is usually much more secure, because it draws entropy straight from the operating system. These digital keys are very rarely seen by the users of bitcoin. Take the first four bytes of the second SHA hash; this is the checksum. Ownership of bitcoin is established through digital keys , bitcoin addresses , and digital signatures. It has a unique and specific number an address. Thanks a lot. These two facts connected together mean that someone who knows your private key can steal from you.
The user can confidently use the same private key again and. Cryptography can also be used to prove knowledge of a secret without revealing that secret digital signatureor prove the authenticity of data digital fingerprint. Finally, CryptoSlate takes no responsibility should you lose money trading cryptocurrencies. Most bitcoin implementations use the OpenSSL cryptographic library to do the elliptic curve math. The more I read here, the more I wonder about cryptos. Starting with amd 6276 monero zcash zen cash private key in the bitmain store how to mine bitshares of a randomly generated number kwe multiply it by a predetermined point on the curve called the generator point G to produce another point somewhere else on the curve, which is the corresponding public key K. This is a blockchain account. Hi Sudhir, great article thank you. Private keys must remain secret. That brings us to the formal specification of our generator library. In bitcoin, most of the data presented to the user is Base58Check-encoded to make it compact, easy how to mine monero amd gpu how to mine monero without a pool read, and easy to detect errors. Mobile and desktop wallets usually also generate a private key for you, although they might have the option to create a wallet from buy one bitcoin example private key own private key. The format you use depends on how you need to use the private key.
Which private key format is this? You can encrypt in the wallet and a public store can be hacked. Instead, there is a shared object that is used by any code that is running in one script. Thank you. Breadwallet CoPay Edge Jaxx Bitpie Blockchain In this kind of wallet, your keys are held by someone else, and if that gets hacked or stolen, your bitcoins are gone. Now, bitaddress. Or, she could generate a vanity address that starts with 1Kids, to make it more distinctive. Not if they do what I do. Our writers' opinions are solely their own and do not reflect the opinion of CryptoSlate. What does that mean for us?