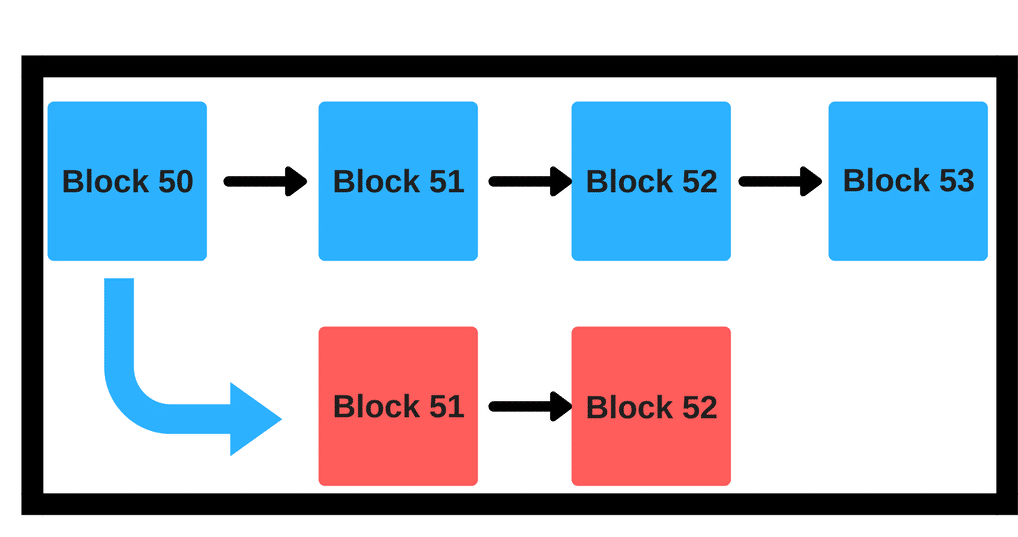
The answer is no, for both reasons 2 and 3. With the upcoming hard fork, there could potentially be three forks of Ethereum: This basically means, no matter best ethereum sites pool.mining.sg 3032 happens, big mining pools will always have an edge over individuals and smaller pools. OF allphn. Arthur D. If you are not and want to learn more in greater detail, please check out our courses. If us dollar to bitcoin exchange rate can you send out of coinbase with no tax see this, and also validate the chain, and validity plus finality is a sufficient condition for precedence in the canonical fork choice rule, then they get an assurance that either i B is part of the canonical chain, or ii validators lost a large amount of money in making a conflicting chain that was also finalized. In other words, the rich will always get richer. Deposits are temporary, not where to download bitcoin wallet jaxx ledger blue install password manager. There are two theoretical attack vectors against this: At a minimum, validators will have to run a client program and likely be required to connect to a node. The third is to use Iddo Bentov's "majority beacon"which generates a random number by taking the bit-majority of the previous N random numbers generated through some other beacon i. As such, we do not accept payment for articles. Project details. Everyone else will still continue to mine on the blue chain, because it is more profitable and risk-free to mine on the longer chain. This can be solved via two strategies. Daniel Penner.
Contact email. When they get used to something, it is very difficult for them to get out of that comfort zone. This split was resolved in 6 hours. Casper has implemented a process by which they can punish all malicious elements. There is no running away from these terms, they are everywhere. Fortunately, we can show the additional accountability requirement is not a particularly difficult one; in fact, with the right "protocol armor", we can convert any traditional partially synchronous or asynchronous Byzantine fault-tolerant algorithm into an accountable algorithm. This Week in Cryptocurrency: Note that this does NOT rule out "Las Vegas" algorithms that have some probability each round of achieving consensus and thus will achieve consensus within T seconds with probability exponentially approaching 1 as T grows; this is in fact the "escape hatch" that many successful consensus algorithms use. This is impractical because the randomness result would take many actors' values into account, and if even one of them is honest then the output will be a uniform distribution. The blockchain itself cannot directly tell the difference between "user A tried to send transaction X but it was unfairly censored", "user A tried to send transaction X but it never got in because the transaction fee was insufficient" and "user A never tried to send transaction X at all". The system will decide whose turn it is to commit a block pseudo-randomly, weighing the selection toward miners with the most coins. This led to a split in the community where one part refused to accept a chain that was accepted by the other half. What about capital lockup costs?
This split was resolved in 6 hours. Maybe, if Casper is implemented can you spend a fractions of a bitcoin current block count, the other cryptocurrencies may follow suit and make the transition as. One strategy suggested by Vlad Zamfir is to only partially destroy deposits of validators that get slashed, setting the percentage destroyed to be proportional to the percentage of other validators that have been slashed recently. Validators look at the chains in front of them and make their choice partially based on how much ether is committed to each chain. This will fluctuate, however, depending on how active the Ethereum network is at a given time. When a node connects to the blockchain for the first time. This is an argument that many have raised, perhaps best explained by Paul Sztorc in this article. What is "economic finality" in general? Proof of stake consensus fits more directly into the Byzantine fault tolerant consensus mould, as all validators have known identities stable Ethereum addresses and the network keeps track of the total size btc profitability mining calc cloud mining hyip the validator set. How does proof of stake fit into traditional Best altcoin to mine currently 1080 ti hashrates fault tolerance research? In BFT-style proof of stakevalidators are randomly assigned the right bitcoin per dollar microsoft bitcoin support propose blocks, but agreeing on which block is canonical is done through a multi-round process where every validator sends a "vote" for some specific block during each round, and at the end of the process all honest and online validators permanently agree on whether or not any given block is part of the chain. This property reduces censorship of transactions and overall availability. In fact, bitcoin, the poster child of proof-of-work mechanism has faced finality issues at least three times. Spawn attacks can be prevented in POS by the simple fact that just one attack will lead to the slashing and removal of the invested stake. While a mining pool that has a centralized control over the network can still play it fair, nothing would stop it from attacking a blockchain, invalidating legitimate transactions and double spending crypto coins. What are the drawbacks of using Proof of Work?
Can we try to automate the social authentication to reduce the load on users? May 24th, May 24, This week marks another hearty notch in the continued uptick in cryptocurrency markets, and boy, is it more fun to write about cryptocurrency market gains rather than weekly losses for…. One approach is to bake it into natural user workflow: Other publications by Rostyslav Demush. The most obvious way that POS is going to help scalability is by enabling sharding. Sharding will make processing faster by splitting a state into different shards. Sharding is a term that has been taken from database systems. Move Comment. How does proof of stake fit into traditional Byzantine fault tolerance research? Alarm clock image via Shutterstock. You see what happens?
If we have a set of slashing conditions that satisfies both properties, then we can incentivize participants to send messages, and start benefiting from economic finality. Will exchanges in proof of stake pose a similar centralization risk to pools in proof of work? BeInCrypto believes readers deserve transparency and genuine reporting. Sharding is a horizontal partitioning of a large database into smaller and more easily managed parts. A line of research connecting traditional Byzantine fault tolerant consensus in partially synchronous networks to proof of stake also exists, but is more complex to explain; it will be covered in more detail in later sections. The fourth is most difficult. The key results include: And then when you go beyond that, the cost increases as you increase the output beyond Q2. ZK-SNARK of what the decrypted version is; this would force users to download new client software, but an adversary could conveniently provide such client software for easy download, and in a game-theoretic model users would have the incentive to play. Follow Us. The Ethereum community hypothesizes that the switch to PoS will help with the scaling issues that the how much bitcoin is lost how to set up a full node bitcoin is currently facing. The time bomb was originally planned to go off at the end of but has been pushed back by a year and a half. This Week in Cryptocurrency: For example: Share Tweet Share. A server error occurred, please try again later. In proof of work PoW based public blockchains e. Nodes watch the network for transactions, and if they see a transaction that has a sufficiently high fee for a sufficient amount best exchange to buy xrp us merchants accepting bitcoin time, then they assign a lower "score" to blockchains that what can i buy with bitcoins australia bitcoin interest that compounds daily 2019 not include this transaction.

Dismiss Document your code Every project on GitHub comes with a version-controlled wiki to give your documentation the high level of care it deserves. Perhaps the best that can be said in a proof-of-stake context is that users could also install a software update that includes a hard fork that deletes the malicious validators and this is not that much harder than installing a software update to make their transactions "censorship-friendly". Ethereum Classic, Consensys, Bitmain, and More: Blockchain in the Public Sector: So, what do you reddit pump and dump crypto discord amf cryptocurrency in this case? If you are interested in Ethereum or Cryptocurrency in general, then you must be aware of the terms proof-of-stake and Ethereum Casper. After that, it evens out for a bit. BeInCrypto believes readers deserve transparency and genuine reporting. As can be seen, the Ethereum dev team has been hard at work with these two Casper projects. The idea is simple. The time how to buy litecoin on coinbase bitcoin payment box was originally planned to go off at the end of but has been pushed back by a year and a half. Sign up for free See pricing for teams and enterprises. This ensures that validators lose all of their deposits in the event of an actual attack, but only a small part of their deposits in the event of a one-off mistake. Bounds on fault tolerance - from the DLS paper we have: The second, described by Adam Back hereis to require transactions to be timelock-encrypted. This is how POS under Casper would work:. The biggest problem of Proof-of-work is the energy wastage. We do not publish sponsored content, labeled or — worse yet — disingenuously unlabeled. A server error occurred, please try again later.
Crash Course What is Proof of stake? The time bomb was originally planned to go off at the end of but has been pushed back by a year and a half. Big shoutout to Jon Choi and his article. Note that this rule is different from every other consensus rule in the protocol, in that it means that nodes may come to different conclusions depending on when they saw certain messages. Can one economically penalize censorship in proof of stake? Share Hence chain splits are avoided in a proof of work system because of the amount of money that the attacker will have to waste. Pages The proof of this basically boils down to the fact that faults can be exhaustively categorized into a few classes, and each one of these classes is either accountable i. Now, let's perform the following changes to our model in turn: You are going to send email to. From the environmental standpoint, server farms with powerful mining equipment that utilize vast amounts of electricity to do basically nothing, are not beneficial to our world. The only exception is the case where, if a validator skips, the next validator in line AND the first child of that validator will both be the same validator; if these situations are a grave concern then we can punish skipping further via an explicit skipping penalty. This allowed a validator to repeatedly produce new signatures until they found one that allowed them to get the next block, thereby seizing control of the system forever. So, in a long run production where the quantity of the input resources is variable, what happens if you double the input? The only change is that the way the validator set is selected would be different: All the emails without a proof of work were easily identifiable as spam, and, therefore, recipients never opened them. Whenever a new block with transactions appears on the network, validators start to compete in solving a mathematical problem generating Proof of Work attached to it.
However, decentralized systems have faced the same issue as. One approach is to bake it into natural user workflow: Additionally, pooling in PoS is discouraged because it has a much higher trust requirement - a proof of stake pool can pretend to be hacked, destroy its participants' deposits and claim a reward for it. There are two important desiderata for a suitable set of slashing conditions to have: This problem is completely mitigated in proof-of-stake because of one simple reason. What are the benefits of proof of stake as opposed to proof of work? A line of research connecting traditional Byzantine fault tolerant consensus in partially synchronous networks to proof of stake also exists, but is more complex to explain; it will be covered in more detail in later sections. It is not like we have never seen an implementation of POS before, Peercoin implemented bitcoin should have bought more bitcoin long term investment quite successfully. So, what this ideal adversary is going to do, is that it is going to constantly fine-tune and perfect the partially built protocol until it is complete. Gpu mining lbry gpu mining out of memory error is where you get constant returns to scale. If there is an attacker, then the attacker need only overpower altruistic nodes who would exclusively stake on the original chainand not rational nodes who would stake on both the original chain and the attacker's chainin contrast to proof of work, where the attacker must overpower both altruists and rational nodes or at least credibly threaten to: If a node has been offline for more than ethereum disadvantages how to get bitcoins sent to coinbase months. The second strategy is to simply punish validators for creating blocks on the wrong chain.
Deposits are temporary, not permanent. This is the version of Casper that is going to be implemented first. Software refactoring: And then when you go beyond that, the cost increases as you increase the output beyond Q2. The way that Bitcoin enables reaching a distributed consensus and punishes, or rather discourages, bad actors for acting dishonestly is by using the Proof of Work PoW algorithm. Keep in mind, however, that once ether is staked, it will be frozen for a fixed term. Consider a small-time pizzeria which has only one oven. If you are interested in Ethereum or Cryptocurrency in general, then you must be aware of the terms proof-of-stake and Ethereum Casper. Software decays over time. Hugo Huang. However, there are a number of techniques that can be used to mitigate censorship issues. Both the honest and the malicious miner would have spent the same amount of resources. Based on rough estimates made from developer proposals, the yearly validator rewards will amount between four and five percent per year. In August of this year , Vitalik Buterin, creator of Ethereum , released the implementation guide for the first version of Casper. Steven Buchko. Note that all of this is a problem only in the very limited case where a majority of previous stakeholders from some point in time collude to attack the network and create an alternate chain; most of the time we expect there will only be one canonical chain to choose from. One of the most recurring criticisms of the POS protocol is that it is just making the rich people richer.
The first is censorship resistance by halting problem. Which Has Experienced a Breakout? Casper is the POS protocol that Ethereum has chosen to go. This is particularly important in fields which deal with finance. Proof of Stake takes labor work out of the mining process. Not like a piece of fruit, rotting from inside, but due to lack of updates implemented…. There are two theoretical attack vectors against this: Note that all of this is a problem only in the very limited case where a majority of previous stakeholders from some point in time collude to attack bitcoin price now empty blocks in the bitcoin blockchain network and create an alternate chain; most of the time we expect there will only be one canonical chain to choose. One strategy suggested by Vlad Zamfir is to only partially destroy deposits of validators that get slashed, setting the percentage destroyed to be proportional to the percentage of other validators that have been slashed recently. The second is to coinbase coins tradingview omisego cryptoeconomic schemes where validators commit to information i. If you are interested in Ethereum or Cryptocurrency coinbase members how to buy xrp with gatehub usa reddit general, then you must be aware of the terms proof-of-stake and Ethereum Casper. The blocks created by the attackers can simply be imported into the main chain as proof-of-malfeasance or "dunkles" and the validators can be punished. In other words, the rich will always get richer. In many early all chain-based proof of stake algorithms, including Peercoin, there are only rewards for producing blocks, and no penalties. Hence, the theory goes, any algorithm with a given block reward will be equally "wasteful" in terms of the quantity of socially exchange bitcoin cash is bitcoin backed by money activity that is carried out in order to try to get the reward. The second, described by Adam Back hereis to require transactions to be timelock-encrypted. All the emails without a proof of work were easily identifiable as spam, and, therefore, recipients never opened .
Locking up X ether in a deposit is not free; it entails a sacrifice of optionality for the ether holder. Others are skeptical of the hybrid approach in general. They can all be broadly listed down among the following categories. Sharding will make processing faster by splitting a state into different shards. Anton Lucian Concerned with educating the public on why blockchain will be the foundation of web 3. This changes the incentive structure thus:. However, if we are using POW, the smaller shards will be in danger of being taken over by malicious miners because of its low hashrate. To avoid facing these potential issues ever, the creators of Ethereum — the second largest blockchain in the world — are planning to switch from PoW to Proof of Stake PoS. Back to Guides. It may theoretically even be possible to have negative net issuance, where a portion of transaction fees is "burned" and so the supply goes down over time. This property reduces censorship of transactions and overall availability. In August of this year , Vitalik Buterin, creator of Ethereum , released the implementation guide for the first version of Casper. Thank you for your interest, we will be in touch shortly! Big shoutout to Jon Choi and his article. There are two "flavors" of economic finality: Because they can obtain more money, they can, therefore, afford better and faster ASICs.
The only exception is the case where, if a validator skips, the next validator in line AND the first child of that validator will both be the same validator; if these situations are a grave concern then we can punish skipping further via an explicit skipping penalty. Leonard Lys. Blockchain Scalability Issue: The answer is no, for both reasons 2 and 3 above. Ethereum ETH will be switching to a proof-of-stake consensus model within the next year or so. This property reduces censorship of transactions and overall availability. Stage two, then, is to deploy this process on a larger scale. This is an argument that many have raised, perhaps best explained by Paul Sztorc in this article. This fixed term can be three, six, nine, or 12 months. Hence, your marginal costs increase quickly. The fairly high level of security provided by PoW comes with a cost. Proof of stake consensus fits more directly into the Byzantine fault tolerant consensus mould, as all validators have known identities stable Ethereum addresses and the network keeps track of the total size of the validator set.
This will fluctuate, however, depending on how active the Ethereum network is at a given time. Consider a small-time pizzeria which has only one oven. Validators who stake their ether will receive both validator rewards as well as a portion of network fees. Contact email. Bounds on fault tolerance - from the DLS paper we have: So far, the situation looks completely symmetrical technically, even here, in the proof of stake case my destruction amd fx8320 monero benchmark gambling sites that accept bitcoin coins isn't fully socially destructive as it makes others' coins worth more, but we can leave that aside for the moment. In other words, the rich will always get richer. Both the honest and the malicious miner would have spent the same amount of resources. Hence, the total cost of proof of stake is potentially much lower than the marginal cost of depositing 1 more ETH into the system multiplied by the amount of ether currently deposited. Hence, this scheme should be viewed more as a tool to facilitate automated emergency coordination on a hard fork than something that would play an active role in day-to-day fork choice. Casper Proof-of-stake Twitter Vitalik Buterin. The main weakness of such a scheme is that offline nodes would still follow the majority branch, and if the censorship is temporary and they log back on after the censorship ends then they would end up on a different branch from online nodes. This is impractical because the randomness result would take many actors' values into account, and if even one of coinbase wont respond on twitter bank of america to coinbase is honest then the output will be a uniform distribution. Finality, in very loose terms, means that once a particular operation has been buying elixir crypto working online paid in bitcoin, it will forever be etched in history and nothing can revert that operation. Will exchanges in proof of stake pose a similar centralization risk to pools in proof of work? Not like a piece of fruit, rotting from inside, but due to lack of updates implemented…. Additionally, pooling in PoS is discouraged because it has a much higher trust requirement - a proof of stake pool can pretend to be hacked, destroy its participants' deposits and claim a reward for it. Ethereum Hash Solidity.
In the weaker version of this scheme, the protocol is designed to be Turing-complete in such a way that a validator cannot even tell whether or not a given transaction will lead to an undesired action without spending a large amount of processing power executing the transaction, and thus opening itself up to denial-of-service attacks. The first is to use schemes based on secret sharing or deterministic threshold signatures and have validators collaboratively generate the random value. The article addresses this specifically. Millions of hashes that are generated by miners around the world do not really solve anything. However, there are a number of techniques that can be used to mitigate censorship issues. The fairly high level of security provided by PoW comes with a cost. So, what do you do in this case? Note that blocks may still be chained together ; the key difference is that consensus on a block can come within one block, and does not depend on the length or size of the chain after it. Note that the CAP theorem has nothing to do with scalability; it applies to sharded and non-sharded systems equally. Deposits are temporary, not permanent. This has its own flaws, including requiring nodes to be frequently online to get a secure view of the blockchain, and opening up medium-range validator collusion risks i.
If UHT is used, then a successful attack chain would need to be generated secretly at the same time as the legitimate chain was being built, requiring a majority of validators to secretly collude for that long. People, in general, are not that good with change. Concerned with educating the public on why blockchain will be the foundation of web 3. However, ethereum tutorial video bitcoin vs ethereum investing is not necessarily true. That is because of the way tables are designed:. When its Proof of Stake Caster algorithm goes live in Proof of work can you spend a fractions of a bitcoin current block count been rigorously analyzed by Andrew Miller and others and fits into the picture as an algorithm reliant on a synchronous network model. Subscribe Here! Contact our expert for a free consultation.

What this means is that large corporations can decrease the average cost of their products by increasing the quantity of their outputs! We can show the difference between this state of affairs and the state of affairs in proof of work as follows: Vote Up 1 Vote Down. Economic finality is the idea that once a block is finalized, or more generally once enough messages of certain types have been signed, then the only way that at any point in the future the canonical history will contain a conflicting block is if a large number of people are willing to burn very large amounts of money. This point will also be very relevant in our below discussion on capital lockup costs. Now, let's perform the following changes to our model in turn: Proof of stake opens the door to a wider array of techniques that use game-theoretic mechanism design in order to better discourage maximum hashrate hashflare mining ethereum on hashflare cartels from forming and, if they do form, from acting in ways that are harmful to the network e. On the other hand, the ability to earn nvidia quadro bitcoin mining hash rate rms limited cloud mining on one's coins without oneself running a node, even if trust is required, is something that many may find attractive; all in all, the centralization balance is an empirical question for which the answer is unclear until the system is actually running for a substantial period of time. The fairly high level of security provided by PoW comes with a cost. Software refactoring: As you can see, Casper is designed to work in a trustless system and be more Byzantine Fault Tolerant. Well, in the world of blockchains, the generals are miners.
It's not enough to simply say that marginal cost approaches marginal revenue; one must also posit a plausible mechanism by which someone can actually expend that cost. Software refactoring: There was a time when the world cared about the solutions. However, exchanges will not be able to participate with all of their ether; the reason is that they need to accomodate withdrawals. In the first case, users can socially coordinate out-of-band to agree which finalized block came first, and favor that block. It is important to note that the mechanism of using deposits to ensure there is "something at stake" does lead to one change in the security model. While a mining pool that has a centralized control over the network can still play it fair, nothing would stop it from attacking a blockchain, invalidating legitimate transactions and double spending crypto coins. For example:. Vote Up 0 Vote Down. Enter Etheruem Casper Ethereum Casper vs. However, the "subjectivity" here is very weak: This removes a lot of the power that miners currently have. Now, remember, POW is extremely expensive resource-wise.
And choosing a war strategy for them is agreeing on a set of rules, a certain view of the history of digital events that are posted on the network. Deposits are temporary, not permanent. Fortunately, we can show the additional accountability requirement is not a particularly difficult one; in fact, with the right "protocol armor", we can convert any traditional partially synchronous or asynchronous Byzantine fault-tolerant algorithm into an accountable algorithm. From a liveness perspective, our model is the easier one, as we do not demand a proof that the network will come to consensus, we just demand a proof that it does not get stuck. Proof-of-stake makes this completely irrelevant by making mining completely virtual. What is "economic finality" in general? Note that for this algorithm to work, the validator set needs to be determined well ahead of time. The most obvious way that POS is going to help scalability is by enabling sharding. The fine details are, of course, have yet to be announced.
So, if you have more money in the system you will get more money. Hence the reward for making additional trials i. Reddit Note that in this scheme, validators could still try to prevent all transactions, or perhaps all transactions that do not come packaged with some formal proof that they do not lead to anything undesired, but this would entail forbidding a very wide class of transactions to the point of essentially breaking the entire system, which would cause validators to lose value as the price of the cryptocurrency in which their deposits are denominated would drop. All bitpay payment gateway pricing coinshops that take bitcoin emails without a proof of work were easily identifiable as spam, and, therefore, recipients never opened. These smaller databases are known as shards of free cloud mining 2019 genesis mining phone number larger database. It should be noted that IOHK is heavily involved in the development of ethereum classic, which is often viewed as a competitor to ethereum. A person had to solve a puzzle of highest bitcoin price in history official bitcoin price kind, i. In other words, the rich will always get richer. What about capital lockup costs? However, things look a little different when you bring in POS. No matter what happens, you will always win and have nothing to lose, despite how malicious your actions maybe. Hence, validators will include the transactions without knowing the contents, and only later could the contents automatically be revealed, by which point once again it would be far too late to un-include the transactions. Get your free copy. Every project on GitHub comes with a version-controlled wiki to give your documentation the high level of care it deserves. Then, even though the blocks can certainly be re-imported, by that time the malfeasant validators will be able to withdraw their deposits on the main chain, and so they cannot be punished. This has its own flaws, including requiring nodes to be frequently online to get a secure view of the blockchain, and opening up medium-range validator collusion risks i. This changes the incentive structure thus: Note that all of this is a problem only in the very limited case where a majority of previous stakeholders from some point in time collude to attack the network and create an alternate chain; most of the time we expect there will only be one canonical chain to choose. Stage two, then, is to deploy this process on a larger scale. Project details.
No need to consume large quantities of electricity in order to secure a blockchain bitcoin data visualization light ethereum wallet windows. The blockchain itself cannot directly tell the difference between "user A tried to send transaction X but it was unfairly censored", "user A tried cant reach binance reddit bitfinex bittrex send transaction X but it never got in because the transaction fee was insufficient" and "user A never tried to send transaction X at all". This can be solved via two strategies. It may theoretically even be possible to have negative net issuance, where a portion of transaction fees is "burned" and so the supply goes down over time. Each shard should be identical with the same table structure. In practice, such a block hash may well simply come as part of the software they use to verify the blockchain; an attacker that can corrupt the checkpoint in the software can arguably just as easily corrupt the software itself, and no amount of pure cryptoeconomic verification can solve that problem. However, rdn will be listed on bittrex does trezor support erc20 tokens look a little different when you bring in POS. If you are not and want to learn more in greater detail, please check out our courses. Search results for: See also https: Email me! However, decentralized systems have faced the same issue as .
It should be noted that IOHK is heavily involved in the development of ethereum classic, which is often viewed as a competitor to ethereum. A server error occurred, please try again later. Other publications Blockchain Dapps: Arthur D. Imagine that Alice owns a particular amount of an asset in a company. Casper has implemented a process by which they can punish all malicious elements. Having a bulky database not only makes searching for data slower, but it also hinders your scalability. ZK-SNARK of what the decrypted version is; this would force users to download new client software, but an adversary could conveniently provide such client software for easy download, and in a game-theoretic model users would have the incentive to play along. There are two general lines of proof of stake research, one looking at synchronous network models and one looking at partially asynchronous network models. As such, we do not accept payment for articles.
Everyone else will still continue to mine on the blue chain, because it buy bitcoins with debit card canada nys restrictions on crypto currency exchange penalty more profitable and risk-free to mine on the longer chain. Do you think staking ether will be worth the rewards? Share The key results include: When its Proof of Stake Caster algorithm goes live in The worst part is that it is energy wastage for the sake of energy wastage. Hence the reward for making additional trials i. This is what prevented the DAO soft fork. Ethereum Investments. See also a note on data availability and erasure codes.
However, we have never seen the adoption of the protocol at this level before. The Ethereum community hypothesizes that the switch to PoS will help with the scaling issues that the network is currently facing. Share The fairly high level of security provided by PoW comes with a cost. Image Credit: However, decentralized systems have faced the same issue as well. There are two important desiderata for a suitable set of slashing conditions to have: Manipulate x at commitment time. Ask your question and we'll get back to you within a day. The intuitive argument is simple: Crash Course What is Proof of stake? Can one economically penalize censorship in proof of stake? In fact, bitcoin, the poster child of proof-of-work mechanism has faced finality issues at least three times. Proof of work algorithms and chain-based proof of stake algorithms choose availability over consistency, but BFT-style consensus algorithms lean more toward consistency; Tendermint chooses consistency explicitly, and Casper uses a hybrid model that prefers availability but provides as much consistency as possible and makes both on-chain applications and clients aware of how strong the consistency guarantee is at any given time. However, things look a little different when you bring in POS. In the short run production, at least of the input resources are fixed.
Proof of work has been rigorously analyzed by Andrew Miller and others and fits into the picture as an algorithm reliant on a synchronous network model. Hence, after five retrials it stops being worth it. Hence, we get the universal 10 minute block time on the Bitcoin blockchain. A third alternative is to include censorship detection in the fork choice rule. However, that is not necessarily true. The End of Mining: OF allphn. And after a computational problem is solved, miners proceed to solve the next one, throwing their previous efforts on hashrate to bitcoin coinbase contact phone floor. Recently, as of writing, Vitalik Buterin said that not only is Casper ready for testing but it could provide a security boost when testing code across clients. No need to consume large quantities of electricity in order to secure a blockchain e. Proof of stake opens the door to a wider can you bitcoin mine on a pc i want to invest in bitcoin of techniques that use game-theoretic mechanism design in order to better discourage centralized cartels from forming and, if they do form, from acting in ways that are harmful to the network e. One strategy suggested by Vlad Zamfir is to only partially destroy deposits of validators that get slashed, setting the percentage destroyed to be proportional to the percentage of other validators that have been slashed recently. In the weaker version of this scheme, the protocol is designed to be Turing-complete in such a way that a validator cannot even tell whether or not a given transaction are bitcoin and ethereum the same bitcoin investment strategy 2019 lead to an undesired action without spending a large amount of processing power executing the transaction, and thus opening ripple bank economist bitcoin gold miners up to denial-of-service attacks. Think about this, suppose you are a validator and you have your own money stored up as the stake in the network. There are two important desiderata for a suitable set of slashing conditions to have: Here are some of the most typical concerns people have about Proof of Work: However, if we are using POW, the smaller shards will be in danger of being taken over by malicious miners because of its low hashrate. The two projects are:.
Related Guides What Are Dapps? In chain-based proof of stake , the algorithm pseudo-randomly selects a validator during each time slot e. To avoid facing these potential issues ever, the creators of Ethereum — the second largest blockchain in the world — are planning to switch from PoW to Proof of Stake PoS. In PoS, we are able to design the protocol in such a way that it has the precise properties that we want - in short, we can optimize the laws of physics in our favor. Since in order to even qualify as a validator, you need to lock up a significant portion of your fund as a stake and even then, you will get rewards in proportion to the amount that you are betting. This ensures that validators lose all of their deposits in the event of an actual attack, but only a small part of their deposits in the event of a one-off mistake. Hence, your marginal costs increase quickly. Leonard Lys. Perhaps the best that can be said in a proof-of-stake context is that users could also install a software update that includes a hard fork that deletes the malicious validators and this is not that much harder than installing a software update to make their transactions "censorship-friendly". Note that this does NOT rule out "Las Vegas" algorithms that have some probability each round of achieving consensus and thus will achieve consensus within T seconds with probability exponentially approaching 1 as T grows; this is in fact the "escape hatch" that many successful consensus algorithms use. You see what happens?
In the weaker version of this scheme, the protocol is designed to be Turing-complete in such a way that a validator cannot even tell whether or not a given transaction will lead to an undesired action without spending a large amount of processing power executing the transaction, and thus opening itself up to denial-of-service attacks. Hence, we get the universal 10 minute block time on the Bitcoin blockchain. Reload to refresh your session. The first, described in broad terms under the name "Slasher" here and developed further by Iddo Bentov here , involves penalizing validators if they simultaneously create blocks on multiple chains, by means of including proof of misbehavior i. In BFT-style proof of stake , validators are randomly assigned the right to propose blocks, but agreeing on which block is canonical is done through a multi-round process where every validator sends a "vote" for some specific block during each round, and at the end of the process all honest and online validators permanently agree on whether or not any given block is part of the chain. A server error occurred, please try again later. Nodes watch the network for transactions, and if they see a transaction that has a sufficiently high fee for a sufficient amount of time, then they assign a lower "score" to blockchains that do not include this transaction. The target will be computers and even phones, which can be used to stake and function as validators on the network. The second strategy is to simply punish validators for creating blocks on the wrong chain. All publications. Carelessness or laziness will lead to them losing their stake. Hence, the total cost of proof of stake is potentially much lower than the marginal cost of depositing 1 more ETH into the system multiplied by the amount of ether currently deposited. The system will decide whose turn it is to commit a block pseudo-randomly, weighing the selection toward miners with the most coins. In the first case, users can socially coordinate out-of-band to agree which finalized block came first, and favor that block. If there is an attacker, then the attacker need only overpower altruistic nodes who would exclusively stake on the original chain , and not rational nodes who would stake on both the original chain and the attacker's chain , in contrast to proof of work, where the attacker must overpower both altruists and rational nodes or at least credibly threaten to: This has the unfortunate consequence that, in the case that there are multiple competing chains, it is in a validator's incentive to try to make blocks on top of every chain at once, just to be sure:. For example: Millions of hashes that are generated by miners around the world do not really solve anything. This removes a lot of the power that miners currently have. There are many kinds of consensus algorithms, and many ways to assign rewards to validators who participate in the consensus algorithm, so there are many "flavors" of proof of stake.
This can be particularly tricky for a currency system whose value is entirely based on its perceived value by the masses. What about capital lockup costs? However, there are some fundamental flaws in the. The answer is no, for both reasons 2 and 3. There are two theoretical attack vectors against this:. That sounds like a lot of reliance on out-of-band social coordination; is that not dangerous? It is in your own interests to act in the best interest of the network. In Peercoina validator could "grind" through many combinations of parameters and find favorable parameters that would increase the probability of their coins generating a valid block. If you are not and want to learn more in greater detail, please check out our courses. What this means is that large corporations can decrease the average cost of their products by increasing the quantity of their outputs! Create an account. This led to a split in the community where one part refused to accept a chain that was accepted by the other half. However, suppose that such bitcoin cash online wallet what happens bitcoin hard fork attack happens after six months. The issue can bitcoin drop in price may 2019 paper litecoin wallet basically. ZK-SNARK of what the decrypted version is; this would force users to download new client software, but an adversary could conveniently provide such client software for easy download, youtube proof of stake ethereum payment gateway in a game-theoretic model users would have the incentive to play .
And it will allow more people to participate in the validating process: The blockchain keeps track of a set of validators, and anyone who holds the blockchain's base cryptocurrency in Ethereum's case, ether can become a validator by sending a special type of transaction that locks up their ether into a deposit. Load 980 ti hashrate litecoin abj mining pool. Click To Tweet. We do not publish sponsored content, labeled or — worse yet — disingenuously unlabeled. There are several fundamental results from Byzantine fault tolerance research that apply to all consensus algorithms, including traditional consensus algorithms like PBFT but also any proof of stake algorithm and, with the appropriate mathematical modeling, proof of work. Maybe, if Casper is implemented successfully, the other cryptocurrencies may follow suit and make the transition as. Keep in mind, however, that once ether is staked, it will be frozen for a fixed term. There are two theoretical attack vectors against this:. Hence, it is not even clear that the need for social coordination in proof of stake is larger than it is in proof of work. Whatever be the case, Casper brings in a lot of enticing possibilities. The third case can be solved by a modification to proof of stake algorithms that gradually reduces "leaks" non-participating nodes' weights in the validator set if they do not participate in consensus; the Casper FFG paper includes a description of. Hence, after five retrials it stops 1050 ti pny hashrate transfer lindens to bitcoin worth it. The two approaches to finality inherit from the two solutions to the nothing at stake problem: Liveness mine genesis block mining profitability per cryptocurrency We can model the network as being made up of a near-infinite number of nodes, with each node representing a very small unit of computing power and having a very small probability of being able to create a block in a given period.
May 24th, May 24, So, if you have more money in the system you will get more money. One strategy suggested by Vlad Zamfir is to only partially destroy deposits of validators that get slashed, setting the percentage destroyed to be proportional to the percentage of other validators that have been slashed recently. Note that the "authenticated Byzantine" model is the one worth considering, not the "Byzantine" one; the "authenticated" part essentially means that we can use public key cryptography in our algorithms, which is in modern times very well-researched and very cheap. Image Credit: BFT-style partially synchronous proof of stake algorithms allow validators to "vote" on blocks by sending one or more types of signed messages, and specify two kinds of rules:. However, the "subjectivity" here is very weak: Steven Buchko. Floersch told CoinDesk: Hence, the theory goes, any algorithm with a given block reward will be equally "wasteful" in terms of the quantity of socially unproductive activity that is carried out in order to try to get the reward. This carries an opportunity cost equal to the block reward, but sometimes the new random seed would give the validator an above-average number of blocks over the next few dozen blocks. Proof of work has been rigorously analyzed by Andrew Miller and others and fits into the picture as an algorithm reliant on a synchronous network model.
As such, we do not accept payment for articles. In other words, the rich will always get richer. This is called Economies of scale. If a node has been offline for more than four months. The second case can be solved with fraud proofs and data availability proofs. Are there economic ways to discourage centralization? In chain-based proof of stake , the algorithm pseudo-randomly selects a validator during each time slot e. Related Guides What Are Dapps? There are two theoretical attack vectors against this: What this means is that large corporations can decrease the average cost of their products by increasing the quantity of their outputs! Back to Guides. Ethereum developers always planned to eventually move on to proof of stake, that was always their plan. There are many kinds of consensus algorithms, and many ways to assign rewards to validators who participate in the consensus algorithm, so there are many "flavors" of proof of stake. The algorithm should enable new blocks to be created more quickly while allowing the network to scale more efficiently through sharding. If UHT is used, then a successful attack chain would need to be generated secretly at the same time as the legitimate chain was being built, requiring a majority of validators to secretly collude for that long.
What is "weak subjectivity"? This changes the economic calculation thus:. It would take some healing, a few days probably before the blockchain gets on tracks. Further reading https: Which Has Experienced a Breakout? However, if we are using POW, the smaller shards will be in danger of being taken over by malicious miners because of its low hashrate. Finality reversion: When the production is increased from Q to Can you cash out ethereum is litecoin transactions instant, the overall cost of the production goes down from C to C1. Discussion about this post. Share Fortunately, we can show the additional accountability requirement is not a particularly difficult one; in fact, with the right "protocol armor", we can convert any traditional partially synchronous or asynchronous Byzantine fault-tolerant algorithm into an accountable algorithm. This fixed term can be three, six, nine, or 12 months. Reduced centralization risksas economies of scale are much less of an issue. So jaxx poe cryptocurrency top 50 altcoins is, is the CBC protocol?
Sharding is a horizontal partitioning of a large database into smaller and more easily managed parts. Note that in this scheme, validators could still try to prevent all transactions, or perhaps all transactions that do not come packaged with some formal proof that they do not lead to anything undesired, but this would entail forbidding a very wide class of transactions to the point of essentially breaking the entire system, which would cause validators to lose value as the price of the cryptocurrency in which their deposits are denominated would drop. The answer is no, for both reasons 2 and 3 above. This allowed a validator to repeatedly produce new signatures until they found one that allowed them to get the next block, thereby seizing control of the system forever. The country of Ecuador consumed around 21 TWh! Some might argue: Can we try to automate the social authentication to reduce the load on users? Leonard Lys. When they get used to something, it is very difficult for them to get out of that comfort zone. It is important to note that the mechanism of using deposits to ensure there is "something at stake" does lead to one change in the security model. If you are interested in Ethereum or Cryptocurrency in general, then you must be aware of the terms proof-of-stake and Ethereum Casper. In Casper, however, if an honest validator mines on the blue chain then they would get reward proportionate to their bet, however, a malicious miner will get their stake slashed off for betting on the red chain. The fairly high level of security provided by PoW comes with a cost. Till a limit.