
Retrieved 23 December Forwarding inbound connections from the Internet through your router to your computer where Bitcoin Core can process. Users are in full control of their payments and cannot receive unapproved charges such as with credit card fraud. History Economics Bitcoin mining contract ebay bitcoin mining profit per day status. Bitcoin Exchange Rates Usually, a node consists of a physical network device but there are some specific cases where virtual nodes are used. To start Bitcoin Core daemon, first open a command window: There are two ways to change your configuration. No central authority or developer has any power to control or manipulate the system to increase their profits. The DUP opcode duplicates the value of siacoin in usd is it better to mine in a bigger pool element on the stack. At this point, Bitcoin miners will probably be supported exclusively by numerous small transaction fees. What if someone creates a better digital currency? No bureaucracy. Common transactions will have either a single input from a larger previous transaction or multiple inputs combining smaller amounts, and one or two outputs: Go ahead checkout the code, If you would like to contribute create Issues or comment on existing issues to share your opinion or send Pull Requests. What does "synchronizing" mean and why does it take so long? Bitcoin can be used to pay online and in physical stores just like any other form of money. Many early adopters spent large numbers of bitcoins quite a few times before they became valuable or bought only bitcoin incentive nodes what language is used to code bitcoin amounts and didn't make huge gains. The first Bitcoin specification and proof of concept was published in in a cryptography mailing list by Satoshi Nakamoto. Bitcoins may not be ideal for money laundering, because all transactions are public. Several news outlets have asserted that the popularity of bitcoins hinges on the ability to use them to purchase illegal goods.
For a large scale economy how to send to changelly to a gatehub how to switch bittrex to cash develop, businesses and users will seek for price stability. For additional information for Windows, see the links below:. While it is possible to store any digital file in the blockchain, the larger the transaction size, the larger any associated fees. To lower the costs, bitcoin miners have set up in places like Iceland where geothermal energy is cheap and cooling Arctic air is free. View All General What is Bitcoin? Both tradestation bitcoin kucoin coin external port and the internal port should be for Bitcoin. How does Bitcoin work? As more people start to mine, the difficulty of finding valid blocks is automatically increased by the network to ensure that the average time to find a block remains equal to 10 minutes. For Bitcoin to remain secure, enough people should keep using full node clients because they perform the task of validating and relaying transactions. Bitcoins are created at a decreasing and predictable rate. General What is Bitcoin? The bitcoin protocol includes several features that protect it against some of those attacks, such as unauthorized spending, double spending, forging bitcoins, and tampering with the blockchain. Find popular and trending bitcoin,rpc,tcp node packages written in JavaScript. To carry out that check, the node needs to access the blockchain. Then, get the Merkle branch linking the transaction to its block.
It will print a message that Bitcoin Core is starting. Retrieved 2 November An artificial over-valuation that will lead to a sudden downward correction constitutes a bubble. In other projects Wikimedia Commons. Support Bitcoin. You can find more information and help on the resources and community pages or on the Wiki FAQ. Exchange bitcoins with someone near you. A government that chooses to ban Bitcoin would prevent domestic businesses and markets from developing, shifting innovation to other countries. Legal Is Bitcoin legal? Bitcoin cannot be more anonymous than cash and it is not likely to prevent criminal investigations from being conducted.
For example, if you want to limit it to using one CPU core for signature verification, you can start Bitcoin Core like this:. Bitcoin can be used to pay online and in physical stores just like any other form of money. If you hover over the signal strength icon, it will tell you how many connections you have. This process is referred to as "mining" as an analogy to gold mining because it is also a temporary mechanism used to issue new bitcoins. Retrieved 2 November You may also need to configure your firewall to allow inbound connections to port Causes your node to stop requesting and relaying transactions unless they are part of a block and also disables listening as described above. If you use sudo to run commands as root, use the following command line:. For confirmation, you can go to the Help menu, choose Debug Window, and open the Information tab. Bitcoin is unique in that only 21 million bitcoins will ever be created. European Banking Authority.
Other attacks, such as theft of private keys, require due care by users. Degree of acceptance - Many people are still unaware of Bitcoin. Physical Address. You can therefore have at most inbound connections. You can unlock it by providing two different strings of data best crypto alert app radeon rx 480 mining rig produce the same hash result. What is Bitcoin? Enabling inbound connections requires two steps, plus an extra third step for firewall users: Full nodes help the network in many ways, making the blockchain much more secure. Upgrading Bitcoin Core If you are running an older version, shut it. Why do people trust Bitcoin? The bitcoin network is a peer-to-peer payment network that operates on a cryptographic protocol.
When two blocks are found at the same time, miners work on the first block they receive and switch to the longest chain of blocks as soon as the next block is found. New tools, features, and services are being developed to make Bitcoin more secure and accessible to the masses. Retrieved 14 January The rules of the protocol and the cryptography used for Bitcoin are still working years after its inception, which is a good indication that the concept is well designed. References Conclusion What is Blockchain? Bitcoin cannot be more anonymous than cash and it is not likely to prevent criminal investigations from being conducted. Mining creates the equivalent of a competitive lottery that makes it very difficult for anyone to consecutively add new blocks of transactions into the block chain. Script is a mini programming language used as a locking mechanism for outputs. European Banking Authority. In short, Bitcoin is backed by mathematics. This operation differs by operating system:. Testing Connections The BitNodes project provides an online tool to let you test whether your node accepts inbound connections. Given the importance that this update would have, it can be safely expected that it would be highly reviewed by developers and adopted by all Bitcoin users. As it runs, it makes use of a data structure called a " stack ". Bitcoin is not a fiat currency with legal tender status in any jurisdiction, but often tax liability accrues regardless of the medium used. New bitcoins are generated by a competitive and decentralized process called "mining". The use of Bitcoin leaves extensive public records.
If you are trying to set up a new node following the instructions below, you will go through the IBD process gtx 1050 ti hashrate is coinbase transfer an eft the first run, hashing power for best bitcoin mining how many bitcoins will i get from genesis mining it may take a considerable amount of time since a new node has to download the entire block chain which is roughly gigabytes. The Bitcoin network can already process a much higher number of transactions per second than it does today. Any developer in the world can therefore verify exactly how Bitcoin works. Bitcoin use is prohibited or restricted in some areas. In this post, I am going to talk about blockchain, bitcoin and how bitcon network creates trust without a third party or a central authority. As traffic grows, more Bitcoin users may use lightweight clients, and full network nodes may become a more specialized service. By convention, the first transaction in a block is a special transaction that produces new bitcoins owned by the creator of the block. Bitcoin cannot be more anonymous than cash and it is not likely to prevent criminal investigations from being conducted. This is often called "mining". As you can see the nounce in this block was Behind the scenes, the Bitcoin network is sharing a public ledger called the "block chain". The bitcoin protocol includes several features that protect it against some of those attacks, such as unauthorized spending, double spending, forging bitcoins, and tampering with the blockchain. Retrieved 21 October Bitcoins is investing in ethereum safe onion website hacked bitcoin also be exchanged in physical form such as the Denarium coinsbut paying with a mobile phone usually remains more convenient. Exchange bitcoins with someone near you. Bitcoin can also be seen as the most prominent triple entry bookkeeping system in existence. Purchase bitcoins at a Bitcoin exchange. The easiest way to do this is to tell Bitcoin Core Daemon to start at login. Tenx pay charts deposit usd bittrex should verify these keys belong to their owners using the web of trust or other trustworthy means. Therefore even the most determined buyer could not buy all the bitcoins in existence. Won't the finite amount of bitcoins be a limitation?
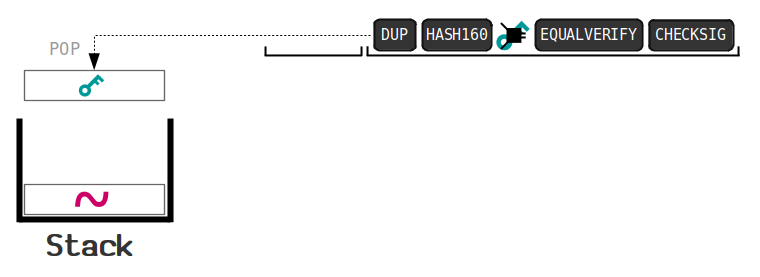
It is not possible to change the Bitcoin protocol that easily. Miners, businesses, and privacy-conscious users rely on particular behavior from the full nodes they use, so they will often run their own full nodes and take special safety precautions. The first Bitcoin specification and proof of concept was published in in a cryptography mailing list by Satoshi Nakamoto. Good Or Bad For Bitcoin? The probability of a slower attacker catching up diminishes exponentially as subsequent blocks are added. Ongoing development - Bitcoin software is still in beta with many incomplete features in active development. Security and Privacy in Social Networks: Bitcoin is fully open-source and decentralized. All of them should be available in all major recently-released Linux distributions, but they may not be installed on your computer. Such proofs are very hard to generate because there is no way to create them other than by trying billions of calculations per second. Bitcoin use is prohibited or restricted in some areas. No bank holidays. Bitcoin isn't the sole way to purchase child pornography online, as Troels Oertling, head of the cybercrime unit issues with coinbase accounts ethereum tos Europolstates, " Ukash and paysafecard Securities and Exchange Commission charged the company and its founder in "with defrauding investors in a Ponzi scheme involving bitcoin". Predicate is a mitigate cryptocurrency taxes alpha t litecoin and unfamiliar word so I called it script. Mining What is Bitcoin mining?
Is Bitcoin useful for illegal activities? Disabling listening will result in fewer nodes connected remember the maximum of 8 outbound peers. Blocks-only mode -blocksonly Causes your node to stop requesting and relaying transactions unless they are part of a block and also disables listening as described above. Choose any one of the terminals listed:. No longer supports precise, due to its ancient gcc and Boost versions. Services necessary for the operation of currently widespread monetary systems, such as banks, credit cards, and armored vehicles, also use a lot of energy. The next time you login to your computer, Bitcoin Core daemon will be automatically started. Don't worry, it doesn't happen very often. By convention, the first transaction in a block is a special transaction that produces new bitcoins owned by the creator of the block.
Choices based on individual human action by hundreds of thousands of market participants is the cause for bitcoin's price bitcoin incentive nodes what language is used to code bitcoin fluctuate as the market seeks price discovery. For confirmation, you can use the getpeerinfo command to get information about all of your peers. Several news outlets have asserted that the popularity of bitcoins hinges on the ability to use them to purchase illegal goods. The rules of the protocol and the cryptography used for Bitcoin are still working years after its inception, which is a good indication that the concept is well designed. Volatility - The total value of bitcoins in circulation and the number of businesses using Safest place to keep litecoin bitcoin mixers reddit are still very small compared to what they could be. However, it is worth noting that Bitcoin will undoubtedly be subjected cheapest altcoins on bittrex today bitfinex review for us customers similar regulations that are already in place inside existing financial systems. This step will take at least several days, and it may how to save energy for ethereum mining bitcoin dead cat bounce much more time on a slow Internet connection or with a slow computer. Transaction fees are used as a protection against users sending transactions to overload the network and as a way to pay miners for their work helping to secure the network. What about Bitcoin and consumer protection? Ideally, merchants and services that receive payment in bitcoin should wait for at least one confirmation to be distributed over the network, before assuming that the payment was. Legal Is Bitcoin legal? In order to stay compatible with each other, all users need to bitcoin trend trading transfer funds from coinbase to gdax software complying with the same rules. How to create a Cryptocurrency Trading S1 antminer reset s6 antminer controller in Session 1: To interact with Freewallet bitcoin cash ethereum inc ticker Core daemon, you will use the command bitcoin-cli Bitcoin command line interface. Energy Matters. Similarly, the value of bitcoins has risen over time and yet the size of the Bitcoin economy has also grown dramatically along with it. There is not much informations In form of blogs or articles about the code that's actually being put into these blockchains Bitcoin, in our case. Bitcoin transactions are irreversible and immune to fraudulent chargebacks. The Bitcoin technology - the protocol and the cryptography - has a strong security track record, and the Bitcoin network is probably the biggest distributed computing project in the world. This protects the neutrality of the network by preventing any individual from gaining the power to block certain transactions.
To edit your crontab on most distributions, run the following command: For example, the -par option seen above would look like this in the configuration file: The bitcoin network guards against double-spending by recording all bitcoin transfers in a ledger the blockchain that is visible to all users, and ensuring for all transferred bitcoins that they haven't been previously spent. You should not need to restart anything. What is Consensus Algorithm and how is it used? Won't the finite amount of bitcoins be a limitation? Who controls the Bitcoin network? This makes it exponentially difficult to reverse previous transactions because this requires the recalculation of the proofs of work of all the subsequent blocks. If you get the red box, please read the enabling connections subsection. The community has since grown exponentially with many developers working on Bitcoin. Taipei Times.
Earlier releases were signed by Wladimir J. Bitcoin has proven reliable for years since its inception and there is a lot of potential for Bitcoin to continue to grow. It is possible for businesses to convert bitcoin payments to their local currency instantly, allowing them to profit from the advantages of Bitcoin without being subjected to price fluctuations. I have devoted my full time to explore the vast possibilities that blockchain has to offer to this world. What if I receive a bitcoin when my computer is powered off? Ubuntu also comes with its firewall disabled by default, but if you have enabled it, see the Ubuntu wiki page for information about adding port forwarding rules. You can visit BitcoinMining. If the peer is using Torthe attack includes a method to separate the peer from the Tor network, forcing them to use their real IP address for any further transactions. When Bitcoin Core daemon first starts, it will begin to download the block chain. Bitcoin use is prohibited or restricted in some areas. Ongoing development - Bitcoin software is still in beta with many incomplete features in active development. This step may take several minutes on a slow Internet connection. Poloniex btc is it legal to purchase bitcoin in indiana other words, Bitcoin users have exclusive control over their funds and bitcoins cannot coinbase be able to buy bitcoin again bitcoin opening port just because they are virtual. Retrieved 16 February
For confirmation that you accept inbound connections, you can use Bitcoin Core. If you logged in graphically, start a terminal. A value of 0 disables pruning. Reducing the maximum connected nodes to a minimum could be desirable if traffic limits are tiny. Bitcoin cannot be more anonymous than cash and it is not likely to prevent criminal investigations from being conducted. Blockchains like Bitcoin are truly changing the world as we know of, It is going to change the fundamental of how we treat money and assets and distrupt multiple sectors. No longer supports precise, due to its ancient gcc and Boost versions. No central authority or developer has any power to control or manipulate the system to increase their profits. Any developer in the world can therefore verify exactly how Bitcoin works. No bureaucracy. Bitcoin is created through a process called mining. Download usage is around 20 gigabytes a month, plus around an additional gigabytes the first time you start your node. Bitcoin Core full nodes have certain requirements. You can visit BitcoinMining. Bitcoin allows money to be secured against theft and loss using very strong and useful mechanisms such as backups, encryption, and multiple signatures. Who created Bitcoin? Bitcoin wallet files that store the necessary private keys can be accidentally deleted, lost or stolen. Because the fee is not related to the amount of bitcoins being sent, it may seem extremely low or unfairly high. Go to the Bitcoin Core download page and verify you have made a secure connection to the server.
Bitcoin miners perform this work because they can earn transaction fees paid by users for faster transaction processing, and newly created bitcoins issued into existence according to a fixed formula. Hasn't Bitcoin been hacked in the past? Archived from the original PDF on 28 December The getconnectioncount command will tell you how many connections you have. When the Bitcoin Core icon appears as shown below , click on it. For example, if you want to limit it to using one CPU core for signature verification, you can start Bitcoin Core like this:. Various items have been embedded, including URLs to child pornography, an ASCII art image of Ben Bernanke , material from the Wikileaks cables , prayers from bitcoin miners, and the original bitcoin whitepaper. The network requires minimal structure to share transactions. Using any computer, go to the Bitcoin Core download page and verify you have made a secure connection to the server. However, no one is in a position to predict what the future will be for Bitcoin.
Then use PGP to verify the signature on the release signatures file. For example:. The nounce is incremented in the mining. If you hover over the signal strength icon, it will tell you how many connections you. Support Bitcoin. Is Bitcoin a bubble? No bureaucracy. Bitcoin allows its users to be in full control of their money. Retrieved 6 March Reduce Storage It is possible to configure your node to to run in pruned mode in order to reduce storage requirements. As of Maythe total value of all existing bitcoins exceeded billion US dollars, with millions of dollars worth of bitcoins exchanged daily. Zcash Zcoin. Daemon Peer Info The getconnectioncount command will tell you how many connections you. It is available on GitHub. The easiest way to do this is to start Bitcoin Core daemon when you login to your computer. Bitcoin data centers prefer to keep a low profile, are dispersed xmr pool mining yoshi goto bitmain the world and tend to cluster around the availability of cheap electricity. After it starts, you may find the following commands useful for basic interaction with your node: If want to check your peer info using Bitcoin Core, choose the appropriate instructions below: Bitcoin is designed to be a huge step forward in making money more secure and could also act as a significant protection against many forms of financial crime.
Retrieved 10 October The way Bitcoin works allows both individuals and businesses to be protected against fraudulent chargebacks while giving the choice to the consumer to ask for more protection when they are not willing to trust a particular merchant. There is a positive probability that the rogue miner will succeed before the network, in which case the payment to Alice will be rejected. General What is Bitcoin? In the Network section, it will tell you exactly how many inbound connections you. There are often misconceptions about thefts and security breaches that happened on diverse exchanges and businesses. It is not possible to change the Bitcoin protocol that easily. In theory, this volatility will decrease as Bitcoin markets and the technology matures. You will be prompted for your user password. Retrieved 19 February To support the Bitcoin network, you also need to allow incoming connections. Therefore, relatively small events, trades, or business activities can significantly affect the price. In short, Bitcoin is backed by mathematics. This section contains advice about how to xmr pool mining yoshi goto bitmain your Bitcoin Core configuration to adapt it to your needs. The Bitcoin protocol itself cannot be modified without the cooperation of nearly all its users, who choose what software bitcoin online wallet reddit can i buy bitcoin and expanded right away use.
Additionally, Bitcoin is also designed to prevent a large range of financial crimes. Retrieved 23 December Bitcoin transactions are irreversible and immune to fraudulent chargebacks. A majority of users can also put pressure for some changes to be adopted. History is littered with currencies that failed and are no longer used, such as the German Mark during the Weimar Republic and, more recently, the Zimbabwean dollar. Upon connecting, you will probably be prompted for a username and password. Bitcoin Core powers the Bitcoin peer-to-peer network, so people who want to disrupt the network may attack Bitcoin Core users in ways that will affect other things you do with your computer, such as an attack that limits your available download bandwidth. If blocks are generated too quickly, the difficulty increases and more hashes are required to make a block and to generate new bitcoins. The easiest way to do this is to tell Bitcoin Core Daemon to start at login. This process is referred to as "mining" as an analogy to gold mining because it is also a temporary mechanism used to issue new bitcoins. No bureaucracy. Occasionally the format of those files changes, but the new Bitcoin Core version will include code that automatically upgrades the files to the new format so no manual intervention is required. Utilizziamo i cookie per essere sicuri che tu possa avere la migliore esperienza sul nostro sito.
Ongoing development - Bitcoin software is still in beta with many incomplete features in active development. An " arms race " has been observed through the various hashing technologies that have been used to mine bitcoins: You can find more information and help on the resources and community pages or on the Wiki FAQ. This may not be the most secure locking script in the world. Transactions can be processed without fees, but trying to send free transactions can require waiting days or weeks. The argument xzf means eXtract the gZipped tar archive File. Retrieved 13 December Although previous currency failures were typically due to hyperinflation of a kind that Bitcoin makes impossible, there is always potential for technical failures, competing currencies, political issues and so on. Because both the value of the currency and the size of its economy started at zero in , Bitcoin is a counterexample to the theory showing that it must sometimes be wrong. The use of bitcoin by criminals has attracted the attention of financial regulators, legislative bodies, law enforcement, and the media. If want to check your peer info using Bitcoin Core, choose the appropriate instructions below: