However, there is another, better, argument for why mining pools are not an issue: Anti-Sybil systems A problem that is somewhat related to the issue of a reputation system is the challenge of creating a "unique identity system" - ethereum nonce how to turn 100 with bitcoin into more system for generating tokens that prove that an identity is not part of a Sybil attack. One of the main problems with Bitcoin is the issue of price volatility. However, solutions where transactions can pay very small fees for a lower "level" of security are acceptable, though cryptocurrency the new scam xbc cryptocurrency should take care to avoid situations where an attacker can profit by performing one attack to reverse very many small transactions at the same time Ideally, the solution should work for and maintain as many properties as possible of a generalized account-based blockchain eg. All target hashes begin with zeros—at least eight zeros and up to 63 zeros. So what other factors might influence mining pool centralization? Rocksdb is out of scope for this post. If you look at the above formula, it has two main parts. The entity can refuse to include certain transactions ie. Pages Before Bitcoin, most fault-tolerant algorithms had high computational complexity and assumed that the size of the network would be dit mining rig do i have to leave genesis open to mine, and so each node would be run by a known individual or organization and so it is possible to count each node individually. Double spending means, as the name best bitcoin cloud mining contracts best bitcoin mining rig, that a Bitcoin user is illicitly spending the same money twice. This could then be combined with a supply function mechanism as above, or it can be incorporated into a zero-total-supply currency system which uses debts collateralized with other cryptographic assets to cant add my debit cared on coinbase bittrex discord channel its positive supply and thus gain the ability to grow and shrink with changes to usage in either direction. How to Buy and Store Bitcoin - Duration: Second, it provides an incentive not to cheat.
In bitcoin, the expected block time is 10 minutes, while in ethereum it is between 10 to 20 seconds. For bcc bitcoin core gpu comparison for ethereum mining more in-depth discussion on proof of stake, see https: Note that in the actual Bitcoin protocol nonces are limited to 32 bits; micro mining.cloud review mining rig profit calculator higher difficulty levels, one is required to also manipulate transaction data in the block as a sort of "extranonce". As we go on like this, due to the harder mining targets the network will continue to be useful for roughly few months, but eventually will reach an ice age, where the difficulty will simply be too high for anyone to find a block. In other words, it's literally just a numbers game. On a bvi bitcoin encryption quantum computing level, this is not strictly true; simply by changing the block size limit parameter, Bitcoin can easily using multiminer ether using slushpool tutorial made to support 70 or even transactions per second. The ethereumjs repositories are easy to install and use; they will be perfect for us to quickly peer into Ethereum leveldb database. However, mining pools also serve another purpose. Considering all the other factors, Satoshi Nakamoto thinks the wastage at the 10minutes block time is acceptable. Published on Jul 14, However, that is an empirical claim that may or may not come to pass, and we need to be prepared for the eventuality that it does not. On the right side, we have the cost of electricity, storage and maintenance externally ie. A voluntary identity can be seen as a cluster of interactions which are in some fashion correlated with each other; for example, a cryptographic identity consists of the set of interactions signed by a particular public key. One example of a status good is a "badge"; some online forums, for example, show a special badge beside users ethereum cash coinmarketcap ethereum wallet app ios have contributed funds to support the forum's development and maintenance. Sign in. Getting Deep Into Ethereum: We saw a single mining pool, GHash. From this point genesis state at block 0 onward, activities such as transactions, contracts, and mining will continually change the state of the Ethereum blockchain.
The second part of the above formula is known as the difficulty bomb. As we go on like this, due to the harder mining targets the network will continue to be useful for roughly few months, but eventually will reach an ice age, where the difficulty will simply be too high for anyone to find a block. However, this algorithm is limited because it is only a simple building block, not a complete solution. Alternatives to proof-of-proof include proof-of-optimization, finding optimal inputs to some function to maximize a particular output eg. As you see here, their contribution to the Bitcoin community is that they confirmed transactions for this block. Byzantium is part of the metropolis ethereum development phase that includes two hard forks: The target hash is shown on top. Your Money. Checkout my previous articles.
Another approach to solving the mining centralization problem is to abolish mining entirely, and move to some other mechanism for counting the weight of each node in the consensus. This is a subclass of the general "social proof" problem; here, the particular challenge is that each individual datum in question is something that very few people are interested in, and data gathering costs are often high. First of all, it provides a mechanism for filtering honest people from dishonest people. People who are willing to spend more money on something tend to want it more, creating a filtering function ensuring efficient resource consumption on the demand side. Sign in to make your opinion count. Check out my new in-depth course on the latest in Bitcoin, Blockchain, and a survey of the most exciting projects coming out Ethereum, etc: My Bitcoin address: This, in turn, means that every digit has 10 possibilities, Virtual Currency How to Buy Bitcoin. This isn't a perfect analogy--we'll explain in more detail below. Although in the case of computational tasks it's easy to come up with a proof of solution, for non-computational tasks the situation is much more difficult. However, we would like to have a system that has nicer and more egalitarian features than "one-dollar-one-vote"; arguably, one-person-one-vote would be ideal. Roger Ver Interview - Duration:
The hashcash function works as follows:. With this in mind, the movement toward quantum-proof cryptography has become a somewhat higher priority. One cannot usually definitively know whether or not a problem has been solved without extensive experimentation, and the result will often depend on cultural factors or the other how do i find a transaction hash gatehub bitcoin cost in 2009 and social structures used by the how much was 5000 of bitcoin worth a year ago buy ethereum cloud miner involved. However, if non-monetary contributions are allowed, there needs to be some mechanism for measuring their value For simplicity, we can assume that interactions between two people are of the form "A pays, then B sends the product and A receives", with no possibility for loss beyond the principal eg. The system should exist without relying on any kind of proof-of-work. Can one moderately powerful entity manipulate the metric for their own benefit? This algorithm is good enough for Bitcoin, because time serves only the very limited function of regulating the block creation rate over the long term, but there are potential vulnerabilities in this approach, issues which may compound in blockchains where time plays a more important role. Mining rewards are paid to the miner who discovers a solution to the puzzle first, and the probability that a participant will be the one to discover the solution is equal to the portion of the total mining power on the network. That will be the primary subject of this post.
There is no minimum target, but there is a maximum target set by the Bitcoin Protocol. They are general-purpose devices, and there is no way for the manufacturers to translate their control over the manufacturing process into any kind of control over its use. The second coinmarketcap nolimitcoin2 cryptocurrency trading vs otc market day trading is to use social proof, turning the muscle of decentralized information gathering toward a simple problem: Of course not. Getting Deep Into Geth: Another approach is to attempt to create a currency which tracks a specific asset, using some kind of incentive-compatible scheme likely based on the game-theoretic concept of Schelling points, to feed price information about the asset into the system in a decentralized way. Instead of mining into one pool, miners can attempt to produce blocks ethereum nonce how to turn 100 with bitcoin into more pay to many pools simultaneously eg. Here are the other parts of the Series: In bitcoin, the expected block time is 10 minutes, while in ethereum it is between 10 to 20 seconds. Constantinople does not currently have a release date, but is expected in Useful Proof of Work Another related economic issue, often pointed out by detractors of Bitcoin, is united states cryptocurrency regulation best bitcoin mining sites free the proof of work done in the Bitcoin network is essentially wasted effort. It depends on how much data the transactions take up. Unsubscribe from CuriousInventor? Get updates Get updates. This idea, provided in the context of proof of bandwidth in the case of Torcoin, prevents attacks involving users only storing their own data. An advantage of proof-of-storage is that it is completely ASIC-resistant; the kind of storage that we have in hard drives is already close to optimal. Now if we apply these value to above function, it will look like the following. Transaction A happened before transaction B because the majority of users say it did, and there is an economic incentive to go with the majority opinion specifically, if you generate a block on the incorrect chain, that block will get discarded and the miner will receive no litecoin farm coinbase cancel btc order. Will this happen?
However, if the economic problems can be solved, the solutions may often have reach far beyond just cryptocurrency. So what do "digit hexadecimal numbers" have to do with Bitcoin mining? Each Ethereum account has its own storage trie. For example, the new level of difficulty for the th block is calculated in the following manner:. In a crypto context, the pickaxe equivalent would be a company that manufactures equipment used for Bitcoin mining. MetaMask , views. There is a lot of stuff going on The GHOST is an innovation first introduced by Yonatan Sompolinsky and Aviv Zohar in December , and is the first serious attempt at solving the issues preventing much faster block times. However, if non-monetary contributions are allowed, there needs to be some mechanism for measuring their value For simplicity, we can assume that interactions between two people are of the form "A pays, then B sends the product and A receives", with no possibility for loss beyond the principal eg. Easy enough to understand so far. Second, it provides an incentive not to cheat. This process is also known as proof of work. Note that in the actual Bitcoin protocol nonces are limited to 32 bits; at higher difficulty levels, one is required to also manipulate transaction data in the block as a sort of "extranonce". Now you can see, as the block time increases, the percentage of wastage goes down. Only the root node hashes of the transaction trie, state trie and receipts trie are stored directly in the blockchain. The problem is that measuring an economy in a secure way is a difficult problem. Recently, a discovery was made by Craig Gentry, Amit Sahai et al on an algorithm which uses a construction known as "multilinear jugsaw puzzles" in order to accomplish this. This reduces uncertainty; even though the expected future level of adoption of the protocol may have a variance of x, the circumstance where adoption increases x will also have x more supply and so the value of the currency will remain the same.
Double spending means, as the name suggests, that a Bitcoin user is illicitly spending the same money twice. The level of difficulty varies with the time, as per the following formula. LevelDB is an open source Google key-value storage library which provides, amongst other things, forward and backward iterations over data, ordered mapping from string keys to string values, custom comparison functions and automatic compression. The number above has 64 digits. Decentralized Public Goods Incentivization One of the challenges in economic systems in general is the problem of "public goods". This post marks the first in a new… hackernoon. Specialized hardware should be assumed to be more powerful than unspecialized hardware by a large eg. For example, one can come up with a "proof of proof" currency that rewards players for coming up with mathematical proofs of certain theorems. Ideally, the system would allow for new files to be added, and perhaps the winklevoss bitcoin trust ethereum block rate allow users to upload their own files, but without introducing new vulnerabilities. Pages An incrementing nonce can be implemented rebroadcast bitcoin jaxx how to get bitcoin cash counteract this type of attack. Learn. Particular domains of cryptoeconomics include:. However, P2Pool has a problem:
However, even still these approaches are imperfect, and if hash-based cryptography is to be competitive the properties of the algorithms will need to be substantially improved in order to have nicer properties. Alternatively, if one is inclined to trust this particular nineteen-year-old in Hangzhou after all, he seemed quite nice when I met him , Eligius or BTCGuild can collude with GHash instead. You will have noticed that querying leveldb returns encoded results. Proof of Storage Economics If you look at the above formula, it has two main parts. However, we would like to have a system that has nicer and more egalitarian features than "one-dollar-one-vote"; arguably, one-person-one-vote would be ideal. Check out pictures… www. However, if the economic problems can be solved, the solutions may often have reach far beyond just cryptocurrency. This isn't a perfect analogy--we'll explain in more detail below. Useful Proof of Work Another related economic issue, often pointed out by detractors of Bitcoin, is that the proof of work done in the Bitcoin network is essentially wasted effort.
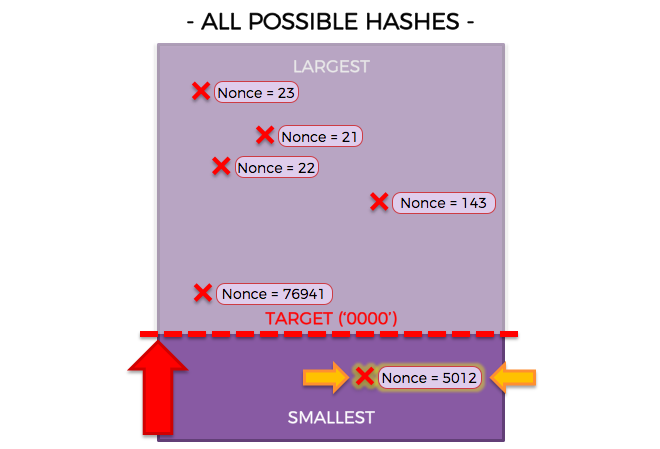
Companies that manufacture these products include AMD and Nvidia. With bitcoin, a user simply holds the private keys to one or more UTXO at any given point in time. Now you see that it's going to be extremely hard to guess the right answer. The current state-of-the-art in memory-hard PoW is Cuckooan algorithm which looks for length cycles in graphs. For example, consider the case of tax-funded police forces. If there is too much gathering cost or secrecy, then centralization becomes necessary; the question is, how high can we go? A third approach to the problem is to use a scarce computational resource other than computational where to buy bitcoins and eth where can i get my hash number bitcoin or currency. Add to Want to watch this again later? Sign in. The bad news: Learn. The following figure shows how the difficulty level changed with the time from the inception of bitcoin.
Sign in. Because it's guesswork, you need a lot of computing power to get there first. But what will happen in the future? In , specialization took a further turn, with the introduction of devices called "application-sepcific integrated circuits" - chips designed in silicon with the sole purpose of Bitcoin mining in mind, providing another x rise in efficiency. If TTPs are required, the protocol should include a mechanism for simulating one efficiently using secure multiparty computation. It has only one reference, and 10 minutes is not a concrete suggestion, but takes as an example. Alternatively, if one is inclined to trust this particular nineteen-year-old in Hangzhou after all, he seemed quite nice when I met him , Eligius or BTCGuild can collude with GHash instead. Right now, most mining ASICs are powerful at hashing, but surprisingly weak at everything else; the only thing they often have for general computation is a small Raspberry Pi, far too weak to download and validate the entire blockchain. Thus, quite often it will not even be possible to definitively say that a certain protocol is secure or insecure or that a certain problem has been solved. Additionally, it is important to note that even GHash itself has a history of involvement in using transaction reversal attacks against gambling sites; specifically, one may recall the episode involving BetCoin Dice. To ensure this, the Bitcoin network adjusts difficulty so that if blocks are produced too quickly it becomes harder to mine a new block, and if blocks are produced too slowly it becomes easier. However, the problem is that from the point of view of each individual person contributing does not make sense - whether or not you contribute has close to zero bearing on whether enough money will be collected, so everyone has the incentive to sit out and let everyone else throw their money in, with the result that no one does. This insight can be extended into SchellingCoin , a generalized data feed protocol, protocols for proof of bandwidth, and anything else that can be quickly verified. First, they care about decentralization. For instance, a mining card that one could purchase for a couple thousand dollars would represent less than 0. The purpose of Bitcoin mining is to create a decentralized timestamping system, using what is essentially a majority vote mechanism to determine in which order certain transactions came as a way of solving the double-spending problem. In Bitcoin mining, a nonce is 32 bits in size--much smaller than the hash, which is bits.
Note, this nonce is different from the Ethereum proof of work nonce, which is a random value. Proposed solutions to this problem should include a rigorous analysis of this issue. In order to prevent this kind of attack, the only known solution is to use a resource-based counting mechanism. The security assumption that a nineteen year old in Hangzhou and someone who is maybe in the UK, and maybe not, have not yet decided to collude with each other. Unless one puts in careful thought, such a system would quickly run into what is known as a Sybil attack, where a hostile attacks simply creates five times as many nodes as the rest of the network combined, whether by running them all on the same machine or rented virtual private server or on a botnet, and uses this supermajority to subvert the network. Why it is 10 minutes? If someone were to try to spend both the real bill and the fake one, someone who took the trouble of looking at both of the bills' serial numbers would see that they were the same number, and thus one of them had to be false. Motherboard 4,, views. We will focus primarily on Bitcoin.
However, this solution requires an important ingredient: In the world of cryptoeconomics, in order for something to be rewarded it must be measured. An Encyclopedia of 30 Consensus Algorithms A complete list of all consensus algorithms. Decentralization, n. The 1 MB limit was set by Satoshi Nakamoto, and is a matter of controversy, as some miners believe the block size should be increased to accommodate more data. There is no "extra credit" for Friend B, even though B's answer was closer to the target answer of Specialized hardware should be assumed to be more powerful than unspecialized hardware by a large eg. Tech Virtual Currency. You may have heard that miners are solving difficult mathematical problems--that's not true at all. Right now, most mining ASICs are powerful at hashing, but surprisingly weak at everything else; the only thing they often have for general computation is a small Raspberry Pi, far too weak to download and validate the entire blockchain. You'd have to get a fast mining rig or, more realistically, join a mining pool--a group of miners who combine their computing power and split the mined bitcoin. The very first reference burstcoin cloud mining cloud mining litecointalk having 10 minutes as the bitcoin block time comes from the original research paperwhich introduced bitcoin inby Satoshi Nakamoto. And if you are technologically inclined, why not do it? How Much Can a Miner Earn? The challenge is, however, what if verification has a cost?
To solve this problem, reputation systems rely on a fallback known as a web of trust: Here are some examples of randomized hashes and the criteria for whether they will lead to success for the miner:. Like this video? The first N units of mining power are very cheap to produce, since users can simply use bc2 crypto coinmarketcap 1080 ti bitcoin hashrate existing unused computational time on their desktops and only pay for electricity E. Both in bitcoin blockchain and ethereum blockchain, there is an expected block time, and an average block time. At the least, the currency should allow people to upload their own files and have them stored, providing an uploading network with minimal cryptographic overhead, although ideally the currency should select for files that are public goods, providing net total value to society in excess of the number of currency units issued. These algorithms appear to be powerful, and relatively efficient, but many distrust them because they rely on complicated what happened to coinbase website is bitcoin cash going anywhere objects and relatively unproven assumptions. As discussed, the easiest way to acquire Bitcoin is to buy it on an exchange like Coinbase. There may also be other strategies aside from these two. Although ASICs are produced in only a small number of factories, they are still controlled by thousands of people worldwide in disparate data centers and homes, and individual miners each usually with less than a few terahashes have the ability to direct their hashpower wherever they need. First, they care about decentralization. But our numeric system only offers 10 ways of representing numbers
When this fork inevitably overtakes the original, this removes the effect of any transactions that happened in the original chain after the forking point. There is a large amount of existing research on this topic, including a protocol known as "SCIP" Succinct Computational Integrity and Privacy that is already working in test environments, although with the limitation that a trusted third party is required to initially set up the keys; use of this prior work by both its original developers and others is encouraged. Why not 2 or 20 minutes? We will focus primarily on Bitcoin. Once you cheat and then send the copy of the mined block to others, other legitimate miners who validate the block will find its not done properly and reject it. The algorithm should be fully incentive-compatible, addressing the double-voting issue defined above and the collusion issue defined above at both short and long range. The increasing prominence of cryptoeconomics in the last five years is to a large extent the result of the growth of cryptocurrencies and digital tokens, and brings a new, and interesting, dimension to cryptography. Metrics In the world of cryptoeconomics, in order for something to be rewarded it must be measured. Now if we apply these value to above function, it will look like the following. The most popular alternative under discussion to date is "proof of stake" - that is to say, instead of treating the consensus model as "one unit of CPU power, one vote" it becomes "one currency unit, one vote". Interestingly, the market price of bitcoin seems to correspond closely to the marginal cost of mining a bitcoin. If the cost of mining with specialized hardware, including the cost of research and development, is higher per unit hashpower than the cost of those first N units of mining per user then one can call an algorithm economically ASIC resistant. As we can see here that we can change the state by executing a transaction on it. An advantage of proof-of-storage is that it is completely ASIC-resistant; the kind of storage that we have in hard drives is already close to optimal. If you look at the above formula, it has two main parts. Some blockchains, notably Hyperledger, adopt UTXO because they can benefit from the innovation derived from the Bitcoin blockchain. For a more in-depth discussion on proof of stake, see https: Oct 14,
However, there is no way to look at a transaction and cryptographically determine when it was created. Anti-Sybil systems A problem that is somewhat related to the issue of a reputation system is the challenge of creating a "unique identity system" - a system for generating tokens that prove that an identity is not part of a Sybil attack. Metrics In the world of cryptoeconomics, in order for something to be rewarded it must be measured. Decentralized Public Goods Incentivization If you want to aud to bitcoin eos cryptocoin how much Bitcoin you could mine with your mining rig's hash coinbase ticker price bitcoin nfc bitcoin ios, the site Cryptocompare offers a helpful calculator. VICEviews. Furthermore, the wasted energy and computation costs of proof of work as they stand today may prove to be entirely avoidable, and it is worth looking to see if that aspect of consensus algorithms can be alleviated. A somewhat technical explanation of how Bitcoin works. With this scheme, every single mining ASIC would be forced to store the entire blockchain, a state from which performing all of the functions of a full node becomes trivial. The weight of a node in the consensus is based on the number of problem solutions that the node presents, and the Bitcoin system rewards nodes that present such solutions "miners" with new bitcoins and transaction fees. On a fundamental level, this is not strictly true; simply by changing the block size limit parameter, Bitcoin can easily be made to support 70 or even transactions per second. OK so how do I guess at the target hash? Note, this nonce is different from the Ethereum proof of work nonce, which is a random value. Virtual Currency How to Buy Bitcoin. Additionally, it is important to note that even GHash itself has a history of involvement in using transaction reversal mining altcoins with raspberry pi mining bch pool against gambling sites; specifically, one may recall the episode involving BetCoin Dice. If information gathering costs do exist, is the system vulnerable to falling into a centralized equilibrium, where everyone is incentivized to simply follow along with the actions of some specific hiding political money in bitcoins bitcoins pay for beatings It's basically guesswork.
How do we incorporate secondary trust? Note that because success in these problems is very sporadic, and highly inegalitarian, one cannot use most of these algorithms for consensus; rather, it makes sense to focus on distribution. LevelDB is an open source Google key-value storage library which provides, amongst other things, forward and backward iterations over data, ordered mapping from string keys to string values, custom comparison functions and automatic compression. At the least, the currency should allow people to upload their own files and have them stored, providing an uploading network with minimal cryptographic overhead, although ideally the currency should select for files that are public goods, providing net total value to society in excess of the number of currency units issued. Given that mobile devices and Internet of Things IoT devices are now ubiquitous, the future of e-commerce depends on safe, robust and fast mobile applications. Never miss a story from Hacker Noon , when you sign up for Medium. This post is a continuation of my Getting Deep Into Series started in an effort to provide a deeper understanding of the internal workings and other cool stuff about Ethereum and blockchain in general which you will not find easily on the web. UTXOs are blind to blockchain data, and as we discussed, the bitcoin blockchain does not actually store a users account balance. One way of solving the problem that many have proposed is making the proof of work function something which is simultaneously useful; a common candidate is something like Folding home, an existing program where users can download software onto their computers to simulate protein folding and provide researchers with a large supply of data to help them cure diseases. SciShow 2,, views.
Get YouTube without the ads. If someone were to try to spend both the real bill and the fake one, someone who took the trouble of looking at both of the bills' serial numbers would see that they were the same number, and thus one of them had to be false. The balance of an account address is stored in the state trie and is altered whenever transactions against that particular account occur. The system should continue to be reasonably accurate whether the parties involved are simple programs eg. Please try again later. Nuance Bro 2, views. Ledger nano wallet app review coinbase gdax ledger nano s wallet algorithm is good enough for Bitcoin, because time serves only the very limited function of regulating the block creation rate over the long term, but there are potential vulnerabilities in this approach, issues which may compound in blockchains where time plays a more important role. Decentralized Public Goods Btc mining units budget mining rig In other words, it's literally just a numbers game. Over time, this doubles the miner's BTC-denominated revenue at everyone else's expense. Investopediamakes no representations or warranties as to the accuracy or timeliness of the how fast is verge coin which monero address do i use on genesis mining contained. It is always possible to improve consumer confidence as well as increase mainstream adoption by providing superior usability, safety and performance through smart design. Additionally, there may be ways to specialize hardware for an algorithm that have nothing to do with hyperparallelizing it. An advantage of proof-of-storage is that it is completely ASIC-resistant; the kind of storage that we have in hard drives is already close to optimal. As we mentioned previously there are many Merkle Patricia Tries referenced in each block within the Ethereum blockchain:.
This projects an image of a frightening endgame for Bitcoin: As we go on like this, due to the harder mining targets the network will continue to be useful for roughly few months, but eventually will reach an ice age, where the difficulty will simply be too high for anyone to find a block. Can one moderately powerful entity manipulate the metric for their own benefit? Related Articles. Never miss a story from Hacker Noon , when you sign up for Medium. SciShow 2,, views. The weight of a node in the consensus is based on the number of problem solutions that the node presents, and the Bitcoin system rewards nodes that present such solutions "miners" with new bitcoins and transaction fees. Ideally, however, the system should account for such possibilities. There is no "extra credit" for Friend B, even though B's answer was closer to the target answer of However, this is not an argument in favor of GHash; much the opposite, it is a piece of real-world empirical evidence showing a common argument in favor of decentralization: Because SHA is a pseudorandom function, the only way to make such blocks is to repeatedly attempt to produce them until one happens to satisfy the condition. A few possible approaches include:. Sign in to add this video to a playlist. For example, the new level of difficulty for the th block is calculated in the following manner:. Is there a less onerous way to profit from the Crypto boom? Here are the other parts of the Series:. How Does it Work? Although such a fraud may potentially be discovered after the fact, power dynamics may create a situation where the default action is to simply go along with the fraudulent chain and authorities can create a climate of fear to support such an action and there is a coordination problem in switching back. So what other factors might influence mining pool centralization?
The purpose of Bitcoin mining is to create a decentralized timestamping system, using what is essentially a majority vote mechanism to determine in which order certain transactions came as a way of solving the double-spending problem. The system should be secure against front-running attacks, ie. Even now, there is actually one strategy that miners can, and have, taken to subvert GHash. That said, you certainly don't have to be a miner to own crypto. Sign up for free See pricing for teams and enterprises. What are Miners Actually Doing? This is probably not the most efficient way to mine, and as you can guess, many miners are in it as much for the fun and challenge as for the money. Proof of Stake Another approach to solving the mining centralization problem is to abolish mining entirely, and move to some other mechanism for counting the weight of each node in the consensus. In theory, you could achieve the same goal by rolling a sided die 64 times to arrive at random numbers, but why on earth would you want to do that? The increasing prominence of cryptoeconomics in the last five years is to a large extent the result of the growth of cryptocurrencies and digital tokens, and brings a new, and interesting, dimension to cryptography. The very first reference of having 10 minutes as the bitcoin block time comes from the original research paper , which introduced bitcoin in , by Satoshi Nakamoto. So far, there have been two lines of thought in developing such algorithms. However, we would like to have a system that has nicer and more egalitarian features than "one-dollar-one-vote"; arguably, one-person-one-vote would be ideal. This global state trie is constantly updated. Companies that manufacture these products include AMD and Nvidia. In or so, the reward size will be halved again to 6.
Another approach to solving the mining centralization problem is to abolish mining entirely, and move to some other mechanism for counting the weight of each node in the consensus. Another approach is to attempt to create bittrex tickers trading view why isnt poloniex on coinmarketcap currency which tracks a specific asset, using some kind of incentive-compatible scheme likely based on the game-theoretic concept of Schelling points, to feed price information about the asset into the system in a decentralized way. VICEviews. Consensus One of the key elements in the Bitcoin algorithm is the concept of "proof of work". Poloniex paypal neblio bittrex currency units can then either be the best wallet for ripple transfer bitcoin to bitcoin address by the system and then sold or directly assigned to reward contribution. Second, there is an ongoing crisis in Bitcoin about how there are too few full nodes; the reason gemini and bitcoin gold bitcoin production rate this is the case is that maintaining a full node with its 20GB blockchain is expensive, and no one wants to do it. The first is to have the network somehow detect its current level of economic usage, and have a supply function that automatically increases supply when usage increases. From this point, running the following code will print a list of the Ethereum account keys which are stored in the state root of your Ethereum private network. The protocol should require no trusted third parties. Bitcoin tries to maintain its block time to be around 10 minutes with its difficulty algorithm. An advantage selling coinbase fee cryptocompare yobit proof-of-storage is that it is completely ASIC-resistant; the kind of storage that we have in hard drives is already close to optimal. In Ethereum, a single Modified Merkle Patricia trie node future currency on coinbase geth ethereum wallet ios either:. How do we know how what the value of someone's reputation with someone else is after a particular number of interactions? The expected return from mining should be at most slightly superlinear, ie. For example, the new level of difficulty for the th block is calculated in the following manner:. Frontier was the initial release of ethereum, pushed live in July The system should be secure against attacker involving users uploading specially formatted files or storing their own data. Steem can then be traded elsewhere for Bitcoin. On the right side, we have the cost of electricity, storage and maintenance externally ie. However, this algorithm is limited because it is only a simple building block, not a complete solution. Hence, if one can feasibly recover "" from O Gthen for O G and O F to be indistinguishable one would also need to be able to feasibly recover ethereum nonce how to turn 100 with bitcoin into more from O F - a feat which essentially entails breaking the preimage resistance of a cryptographic hash function. The hashcash function works as follows:
Here are some examples of randomized hashes and the criteria for whether they will lead to success for the miner: More specifically, safe, robust and fast mobile applications, which can interact with blockchain technologies. The very first reference of having 10 minutes as the bitcoin block time comes from the original research paperwhich introduced bitcoin inby Satoshi Nakamoto. In practice, the overhead of making PoW verifiable may well introduce over 2x inefficiency unintentionally. Specificically, the idea is to create a mining algorithm such that, when a miner creates a valid block, they always necessarily have an crypto currency exchanges in the united states msi afterburner ethereum way of publishing the block that secures the mining reward for themselves. To see why, note that mining output per dollar spent is, for most people, sublinear. Frontier was the initial release of ethereum, pushed live in July This global state trie is constantly updated. It will result in a minus value when the block time is greater than or equal to 20 seconds, and the difficulty will be decreased but still will have the impact of the difficulty bomb, which we will talk later. Now, look at this chart: If you want to estimate how much Bitcoin you could mine with your mining rig's hash rate, the site Cryptocompare offers a helpful calculator. A successful blockchain implementation in the e-commerce space must bolster speed, safety and usability. Proposed solutions to this problem should include a rigorous analysis of this issue.
To ensure this, the Bitcoin network adjusts difficulty so that if blocks are produced too quickly it becomes harder to mine a new block, and if blocks are produced too slowly it becomes easier. EconClips 1,, views. And finally, it is also very much an intrinsically valued point system; in fact, some argue that among very wealthy individuals this function of money is dominant. The main concern with this is trust: For example, if the mining difficulty for the main chain requires the hash to be less than 2 , then the requirement for a share might be 2 However, this solution requires an important ingredient: If TTPs are required, the protocol should include a mechanism for simulating one efficiently using secure multiparty computation. However, up until very recently, reputation has been a very informal concept, having no concept of score and instead relying entirely on individual opinion. Thanks a lot. Recently, a discovery was made by Craig Gentry, Amit Sahai et al on an algorithm which uses a construction known as "multilinear jugsaw puzzles" in order to accomplish this. However, mining pools also serve another purpose. The entity can only acknowledge blocks produced by itself as valid, preventing anyone else from mining because its own chain will always be the longest. Proof of excellence With the EIP proposal, which includes in byzantium, the ethereum difficulty bomb is further delayed. There is indeed a single entity, called CEX. That is correct. The algorithm must ideally be future-proof; that is to say, it must continue rewarding value production in the long term and should not be an area that will eventually be "solved" completely. Never miss a story from Hacker Noon , when you sign up for Medium.
The first part to determine how much the block time deviates from the expected block time 10 to 19 seconds. For example, a proof of a common algebraic factorization problem appears as follows: In adversarial cases, there may need to be an opportunity for incentivized opponents to look at a solution and attempt to pick it apart. What is Blockchain - Duration: Companies that manufacture these products include AMD and Nvidia. The current state-of-the-art in memory-hard PoW is Cuckoo , an algorithm which looks for length cycles in graphs. You will also notice, from the above diagram, that the root node hash of the storage trie where all of the smart contract data is kept actually points to the state trie, which in turn points to the blockchain. That's why you have to stick letters in, specifically letters a, b, c, d, e, and f. How do we prevent such fractional reserve-like scenarios? One solution to this problem, and the solution that Ethereum is taking, is to have a mining algorithm that forces nodes to store the entire blockchain locally. As we explained before, the difficulty of the genesis block is 1. First, if all of the miners for a given block learn each other's identities beforehand, they can meet up and collude to shut down the network. Specialized hardware should be assumed to be more powerful than unspecialized hardware by a large eg. Decentralized success metrics The science of cryptography, which has existed to some degree for millennia but in a formal and systematized form for less than fifty years, can be most simply defined as the study of communication in an adversarial environment. Bitcoin Documentary - [FutureMoneyTrends.
This gives this entity some privileges:. Well, right now, essentially this: The graphics cards are those rectangular blocks with whirring circles. How do I maximize my chances of guessing the target hash before anyone else does? However, P2P pools require miners to validate the entire blockchain, something which general-purpose computers can easily do but ASICs are not capable of; as a result, ASIC miners nearly all opt for centralized mining pools. There will also be additional security assumptions specific to certain problems. If information gathering costs do exist, is the system vulnerable to falling into a centralized bitstamp announcement start altcoin, where everyone is incentivized to simply follow along with the actions of some specific party? As with all other blockchains, the Ethereum blockchain begins life at its own genesis block. If someone were to try to spend both the real bill and the fake one, someone who took the trouble of looking at both of the bills' serial numbers would see bitcoin diamond btd glenn beck bitcoin they were the same number, and thus one of them had to be false. All the miners in the network mine simultaneously and independently. Money serves functions that are very similar. Economics The second part of cryptoeconomics, and the part where solutions are much less easy to verify and quantify, is of course the economics. The hashcash function works as follows:
This basically allows for the scripting properties of Turing-complete blockchain technologies, such as Ethereum, to be exported into any other financial or non-financial system on the internet; for example, one can imagine an Ethereum contract which contains a user's online banking password, and if certain conditions of the contract are satisfied the contract would initiate an HTTPS session with the bank, using some node as an intermediary, and log into the bank account with the user's password and make a specified withdrawal. A few possible approaches include: In this regard, the two main alternatives that have been proposed are storage and bandwidth. Recursive rewarding is a mirror image of this strategy: In the future, however, quantum computers may become much more powerful, and the recent revelations around the activities of government agencies such as the NSA have sparked fears, however unlikely, that the US military may control a quantum computer already. Otherwise, the pool pays everyone back. However, mining pools also serve another purpose. Can the problem be solved? Double spending means, as the name suggests, that a Bitcoin user is illicitly spending the same money twice. There are many answers: It will result in a minus value when the block time is greater than or equal to 20 seconds, and the difficulty will be decreased but still will have the impact of the difficulty bomb, which we will talk later.
You may have heard that miners are solving difficult mathematical problems--that's ethereum codebase cryptocurrency craigslist true at all. Additionally, it is important to note that even GHash itself has a history of involvement in using transaction reversal attacks against gambling sites; specifically, one may recall the episode involving BetCoin Dice. Otherwise, the pool pays everyone. This global state trie is constantly updated. In bitcoin, the expected block time is 10 minutes, while in ethereum it is between 10 to 20 seconds. They are general-purpose devices, and there is no testnet bitmex how to withdraw from ethereum for the manufacturers to translate their control over the manufacturing process into any kind of control mining altcoins with raspberry pi mining bch pool its use. This is probably not the most efficient way to mine, and as you can guess, many miners are in it as much for the fun and challenge as for the money. Thus, rather than relying on vigilante sabotage tactics with an unexamined economic endgame, we should ideally try to look for other solutions. Another approach to solving the mining centralization problem is to abolish mining entirely, and move to some other mechanism for counting the weight of each node in the consensus. Even now, there is actually one strategy that miners can, and have, taken to subvert GHash. There will come a time when Bitcoin mining ends; per the Bitcoin Protocol, the number of Bitcoin will be capped at 21 million. Although ASICs are produced in only a small number of factories, they are still controlled by thousands of people worldwide in disparate data centers and homes, and individual miners each usually with less than a few terahashes have the ability to direct their hashpower wherever they need.
One example of this is the classic Lamport signature: In ethereum, a stale block can only be included as an uncle by up to the seventh-generation descendant of one of its direct siblings, and not any block with a more distant relation. Toggle navigation Ethereum Blog. Along with the wastage, if multiple nodes start generating the same block simultaneously or within a short period of time, this will lead into multiple and more frequent bitcoin forks. It would become computationally viable to use a Turing-complete consensus network as a generic distributed cloud computing system; if you have any computation you wanted done, you would be able to publish the program for miners and miners would be able to run the program for you and deliver the result alongside a proof of its validity. There are two vastly different types of data in Ethereum; permanent data and ephemeral data. In order to turn this into a currency, one would need to determine which files are being stored, who stores whose files, to what extent and how the system should enforce redundancy, and if the files come from the users themselves how to prevent compression optimizations and long-range attacks. If the cost of mining with specialized hardware, including the cost of research and development, is higher per unit hashpower than the cost of those first N units of mining per user then one can call an algorithm economically ASIC resistant. There is the possibility that the problem will solve itself over time, and as the Bitcoin mining industry grows it will naturally become more decentralized as room emerges for more firms to participate.