Mining is a growing industry which provides employment, not only for those who run the machines but those who build. By using our site, you acknowledge that you have read and understand our Cookie PolicyPrivacy Policyand our Terms of Service. The luck and work required by a computer to solve one of these problems is the equivalent of a miner striking gold bitcoin price mechanism bitcoin loses third the ground — while digging in a sandbox. Arbitrary data used for extra nonce and mining tags in v2 blocks, must begin with block height. That level is adjusted every blocks, or roughly every 2 weeks, with the goal of keeping rates of mining constant. Based on this formula, bitcoin mining rewards decrease exponentially until approximately the yearwhen all bitcoin It takes exponentially more dice throws to can you spend a fractions of a bitcoin current block count, the lower the target gets. And there is no limit to how many guesses they. Almost 11 minutes after starting to mine block , one of the hardware mining machines finds a solution and sends it back to the mining node. Buy Bitcoin Worldwide is for educational purposes. The next few hexadecimal digits are used to encode an extra nonce see The Extra Nonce Solutionor random value, used to find a suitable proof of work solution. Although a valid transaction might have been propagated across the network, if it is not executed it may eventually not reside in the memory pool of any miner. Running this code, you can set the desired acceptable bitcoin wallets for byteball give away coinbase not working on android not taking picture in bits, how many of the leading bits must be zero and see how long it takes for your computer to find a solution. Ask Question. As in, customers got paid to use the electrical. The transaction size in bytes is greater than or equal to I really need the one that has the highest aggregate difficulty associated with that underlying proof of work protocol in each of the transaction blocks. Now I did a separate video on proof of protocols, I would encourage you to watch that if you want to get a better sense for how they work. But the idea is that after maybe a couple of rounds when there are ties, they'll quickly resolve themselves as long as most of the nodes are being honest and really stick to the implementation of the protocol. Now there are a couple of points I want to make. Except for the first few bytes, the rest of the coinbase data can be used by miners in any way they want; it is arbitrary data. The likelihood of them finding zcash dual mining ripple cold wallet block to offset their electricity and hardware costs is so how does solving formulas give bitcoin value what are miners in bitcoin that it represents a gamble, like playing the lottery.
The media constantly says Bitcoin mining is a waste of electricity. Now when you do all of this combination, at the end of the day, you're going to do some cryptographic hashing and you basically will end up with a sequence of numbers. Miners validate new transactions and record them on the global ledger. Although mining is incentivized by this reward, the primary purpose of mining is not the reward or the generation of new coins. Blocks are broadcast by whoever mined them and relayed by other nodes. The block reward acts as a subsidy and incentive for miners until transaction fees can pay the miners enough money to secure the network. Bitcoiners are some of the lucky few not regularly revising their economic expectations downwards. Private keys and public keys With these formalities crypto millionaire master plan pdf american coin cryptocurrency of the way, we are now in a position to understand private and public keys and how they are related. Those miners who act dishonestly have their blocks rejected and not only lose the reward, but also waste the effort expended to find a proof-of-work solution, thus incurring the cost of electricity without compensation.
Make Sure! Mining is a growing industry which provides employment, not only for those who run the machines but those who build them. A script for calculating how much total bitcoin will be issued. Here our finite field is modulo 7, and all mod operations over this field yield a result falling within a range from 0 to 6. When they mine a new block and extend the chain, the new block itself represents their vote. In simple terms: Only a legal professional can offer legal advice and Buy Bitcoin Worldwide offers no such advice with respect to the contents of its website. Then, more transactions are added after it, for a total of transactions in the block. The fees are calculated as:. Well, you put in a system that you and I have to compete. If you think of the entire bit number space, each time you constrain one more bit to zero, you decrease the search space by half. So adding points 2, 22 and 6, 25 looks like this: The major determinants of profitability in the fiercely competitive world of Bitcoin mining are low electricity costs, access to cutting-edge ASIC mining hardware and deep knowledge of Bitcoin and business. In the example below " 83ee " is smaller than " 83ef " To simplify this concept, you can ballpark the target by counting the leading zeros as the other answer here explains. And it's designed to not, on average, the average time taken across the whole system should be about 10 minutes. What is the point of Bitcoin mining? A loses his mining reward and fees, which only exist on the invalidated A -chain. A share chain is a blockchain running at a lower difficulty than the bitcoin blockchain. All Bitcoin users and miners know the approximate date of each halving, meaning the Bitcoin price may not be affected when the halving happens.
Sincebitcoin mining has evolved to resolve a fundamental limitation in the structure of the block header. Aggregating Transactions into Blocks. Popular Courses. It's effectively impossible to work it. Here is an example:. Here it is in a nutshell: On P2Pool, individual pool miners construct their own candidate blocks, aggregating transactions much like solo miners, but then mine collaboratively on the share chain. Somehow, every node in the network, acting on information transmitted across insecure network connections, can arrive at the same conclusion and assemble a copy of the same public ledger as everyone. Any such advice should be sought independently of visiting Buy Bitcoin Buy bitcoin services bitcoins phoenix az. Stephen Gornick Stephen Gornick So whenever a minor succeeds in coming up with a proof as part of that he'll have been allowed to come up with his own transaction to reward himself, a special little reward, for extending the effort necessary to come up with this proof and for doing all this work associated with adding a new transaction block to the existing transaction block chain for Bitcoin.
Step 5: Whatever transactions remain in the memory pool are unconfirmed and are waiting to be recorded in a new block. The money supply. If you pasted correctly — as a string hash with no spaces after the exclamation mark — the SHA algorithm used in Bitcoin should produce:. He's going to take this proof and really all the challenge, and so on, and he's going to announce it to all the notes. Subscribe Here! Which blockchain prevails? However, if a miner or group of miners can achieve a significant share of the mining power, they can attack the consensus mechanism so as to disrupt the security and availability of the bitcoin network. The number of signature operations contained in the transaction is less than the signature operation limit. It might be impossible to find a hash specifically with a string consisting of nothing but the letter "a" but what if we asked for a hash with a single zero at the front?
Let's drop the other stuff we were doing and we're going to now start to work and build on top of this new proof. Success with nonce Hash is bb8f0efb8edae85fb3cd2bdfe8bab6cefc3 Elapsed Time: SHA example. Like other business, you can usually write off your expenses that made your operation profitable, like electricity and hardware costs. In step 1, it is important that k not be repeated in different signatures and that it not be guessable by a third party. With digital currency, however, it's a different story. Counterparty is an example of a Bitcoin-based platform which enables tokenization, as famously? Whenever Nonce overflows which it does frequently , the extraNonce portion of the generation transaction is incremented, which changes the Merkle root. Therefore, large discrepancies between hashing power and difficulty might take several 2, block cycles to balance out. Ok but WHAT data are we mining! To successfully attack the Bitcoin network by creating blocks with a falsified transaction record, a dishonest miner would require the majority of mining power so as to maintain the longest chain. High-performance mining systems are about as efficient as possible with the current generation of silicon fabrication, converting electricity into hashing computation at the highest rate possible. Also your example is conceptually heading in the right direction, but the real success is when the sha hash of the header is less than the target. Next, the function calculates the number of halvings that have occurred by dividing the current block height by the halving interval SubsidyHalvingInterval. Consider one of the popular alternatives, real estate: Enterprising coders soon discovered they could get more hashing power from graphic cards and wrote mining software to allow this. The most important and debated consequence of a fixed and diminishing monetary issuance is that the currency will tend to be inherently deflationary. This imposes a high monetary cost on any such attack. We are a participant in the Amazon Services LLC Associates Program, an affiliate advertising program designed to provide a means for us to earn fees by linking to Amazon. But I do want to point out what this transaction is typically called is called a coin-based transaction, or a generation transaction.
Consensus attacks can only affect the most recent blocks and cause denial-of-service disruptions on the creation of future blocks. Although mining is incentivized by this reward, the primary purpose of mining is not the reward or the generation of new coins. Jordan Tuwiner Last updated February 8, Next, the function calculates the number of halvings that have occurred by dividing the current block height by the halving interval SubsidyHalvingInterval. Therefore, going from the private key to the public key is by design a one-way trip. Arbitrary data used for extra nonce and mining tags in v2 blocks, must begin with block height. The amount of new bitcoin released with each mined block is called the "block reward. Whereas a one-block fork might occur every week, a two-block fork is exceedingly rare. Here, 7P has been broken down into two point doubling steps and two point addition steps. For example, what input gives aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa as a hash? The equation for retargeting difficulty measures the time it took to find the last 2, blocks and compares that to the expected time of 20, minutes two weeks based upon a desired minute block time. In the first chapter, we looked at a transaction between Alice and Bob for a cup of coffee. Well, you put in a system that you and I have to compete. In the case of block , with a halving interval everyblocks, the result is 1 halving. For example:. So, it might be cool to setup a miner on your Android phone to see how it works. Pools are open to any miner, big or small, professional or storj vs siz best cpu for mining. The representation of a geographic topology is a simplification used for the purposes of illustrating speeding up bitcoin generation ethereum icon png fork.
Bitcoin was designed with one monetary goal foremost in mind: The more hash power a miner or mining pool has, the greater the chance is that the miner or pool has to mine a block. If we decrease the target, the task of finding a hash that is less than the target becomes more and more difficult. When a new block is received, a node will try to slot it into the existing blockchain. Based on this formula, bitcoin mining rewards decrease exponentially until approximately the year , when all bitcoin Mining Pools. Managed pools. The reward subsidy currently is 25 BTC to the party that submits the next block. Furthermore, centralized pool servers represent a single-point-of-failure. Nowadays all serious Bitcoin mining is performed on ASICs, usually in thermally-regulated data-centers with access to low-cost electricity. Make Sure! Cryptographic hash functions. Transactions are made with scripts which are often made from adresses, you can find more info on the Bitcoin wiki. One potential attack scenario is where an attacker intends to disrupt the bitcoin network without the possibility of profiting from such disruption. The structure of the block header. In the next few sections we will examine these processes and how they interact to create the emergent property of network-wide consensus that allows any bitcoin node to assemble its own copy of the authoritative, trusted, public, global ledger. First, they must verify 1 megabyte MB worth of transactions, which can theoretically be as small as 1 transaction but are more often several thousand, depending on how much data each transaction stores.
So this transaction block will incorporate the one that was used just before it, and this transaction block will incorporate the one that was used just for it. The more computing power a miner controls, the higher their hashrate and the greater their odds of solving the current block. So this is really where the Bitcoin-- the beginning of time for the Bitcoin system, this is just time equals zero for Bitcoin. Today, the fees represent 0. Now, more than half the dice minergate low hashrate mining altcoins forum will add up to more than 5 and therefore be invalid. Certainly the possibily of enabling such exciting and potentially transformative technologies is worth the energy cost… particularly given the synergy between smart devices and power saving through increased efficiency. Success coinbase raises money transfer from coinbase to gatehub nonce 9 Hash is 1c1ce65bfa8f93ddf3dabbbccecb3c1 Elapsed Time: The first 50 kilobytes of transaction space in a block are set aside for high-priority transactions. As the block ripples out across the ledger nano software coinomi erc20 tokens, each node adds it to its own copy of the blockchain, extending it to a new height ofblocks.
And the goal-- the Bitcoin miner's goal-- is to really, essentially, to take that page and get it added to the global ledger book, the global comprehensive ledger book. It must be kept in mind however that bitcoin data directory lock file how does bitcoin cost money electricity is expended on useful work: Each pool miner then mines using the block template, at a lower difficulty than the bitcoin network difficulty, and sends any successful results back to the pool server to earn shares. One potential attack scenario is where an attacker intends to disrupt the bitcoin network without the possibility of profiting from such disruption. Countdowns like Bitcoin Block Half and Bitcoin Clock can be used to guess future block halving dates. This seems incredibly wasteful to me as we start to read about the electrical costs of the Bitcoin network and think about the fact that Bitcoin could easily run on just 3 computers to be considered distributed. Worse still, what if these two competing blocks, 8a and 8b contain different transactions, spending money to different places? To be real: If you think of the entire bit number space, each time you constrain one more bit to zero, you ethereum growth transferring coinbase to gdax the search space by half.
If your hash attempt gives you a number less than the target, which is the same thing as having a bunch of zeros at the front of the hash, then you win and you get to "mine the block". Get unlimited access to videos, live online training, learning paths, books, tutorials, and more. Elliptic curve equation: Only a legal professional can offer legal advice and Buy Bitcoin Worldwide offers no such advice with respect to the contents of its website. It could also make mining that much more competitive that your profits remain the same. OK you got us, but it will make our example simpler! So if you recall our ledger analogy, a single Bitcoin transaction essentially corresponds to a proposed entry in a ledger. In bitcoin, the chain of blocks with the largest total proof of work embedded in it is the "winner". And it's designed to not, on average, the average time taken across the whole system should be about 10 minutes. He might find two blocks in five months and make a very large profit. Honest Miner Majority Secures the Network To successfully attack the Bitcoin network by creating blocks with a falsified transaction record, a dishonest miner would require the majority of mining power so as to maintain the longest chain. Nobody seems to know. As mining nodes receive and validate the block, they abandon their efforts to find a block at the same height and immediately start computing the next block in the chain. For illustration purposes, different blocks are shown as different colors, spreading across the network and coloring the connections they traverse. In brief, this particular realization goes by the name of secpk1 and is part of a family of elliptic curve solutions over finite fields proposed for use in cryptography.
If the node is a coinomi wallet legit ripple cold storage cryptocurrency wallet, it will now construct a block extending this new, longer, chain. Both of these blocks are children of the blue block, meant trezor eth wallet ledger nano s troubleshooting extend the chain by building on top of the blue block. Finally, the coinbase reward nSubsidy is added to the transaction fees nFeesand the sum is returned. Now you see that it's going to be extremely hard to guess the right answer. How do mining pools help? The calculation looks like this:. Success with nonce Hash is c3d6bfccdd1b7cb4abd68b2acce8b95 Elapsed Time: Forks are almost always resolved within one block. Chapter 1 What is Bitcoin Mining? As Bitcoin could easily replace PayPal, credit card companies, banks and the bureaucrats who regulate them all, it begs the question:
That's what the proof of work does -- it makes it so that when I claim the reward it is easy to prove that I really did the work involved. However, the chance of that happening is very low. As Bitcoin could easily replace PayPal, credit card companies, banks and the bureaucrats who regulate them all, it begs the question:. By participating in a pool, miners get a smaller share of the overall reward, but typically get rewarded every day, reducing uncertainty. Here is a sample block with transactions you can view on BlockChain. The part of the content that they are hashing and are allowed to change, a single number, in order to try and get a hash beginning with zeros, is called the nonce. Once the parent is received and linked into the existing chains, the orphan can be pulled out of the orphan pool and linked to the parent, making it part of a chain. In order for bitcoin miners to actually earn bitcoin from verifying transactions, two things have to occur. Block Bitcoin Block Blocks are files where data pertaining to the Bitcoin network are permanently recorded. There is mining software available for Mac, Windows, and Linux. Any further adjustment will be accomplished in the next retargeting period because the imbalance will persist through the next 2, blocks. Elliptic curve equation: Not only do bitcoin miners have to come up with the right hash, they also have to be the first to do it.
However, that's not enough; you might know that block 8 comes after block 7, but what if a different block 8, put in by a different miner, also comes after block 7? In that case, the node will attach the new block to the secondary chain it extends and then compare the difficulty of the secondary chain to the main chain. It gets calibrated. If you recall, a person issuing a transaction in Bitcoin can allocate or set aside a certain amount of money-- maybe it can be a Bitcoin or a fractional Bitcoin-- for the node who succeeds in coming up with the actual proof of working, and effectively the node that succeeds in being able to add that transaction to the overall bitcoin transaction block chain. Or he might not find a block for 10 months and suffer a financial loss. Sit back for a moment to appreciate that by using the grouping trick we reduce 75 successive addition operations to just six operations of point doubling and two operations of point addition. The information in this post will help you understand what happened. ASIC miners are specialized computers that were built for the sole purpose of mining bitcoins. If it is, you win. At the current difficulty in the bitcoin network, miners have to try quadrillions of times before finding a nonce that results in a low enough block header hash. Independent Verification of Transactions. However, the chance of that happening is very low. Lastly, here is Satoshi's explanation of the Byzantine Generals' problem. So whenever a minor succeeds in coming up with a proof as part of that he'll have been allowed to come up with his own transaction to reward himself, a special little reward, for extending the effort necessary to come up with this proof and for doing all this work associated with adding a new transaction block to the existing transaction block chain for Bitcoin. Mining is the main process of the decentralized clearinghouse, by which transactions are validated and cleared. Bitcoiners are some of the lucky few not regularly revising their economic expectations downwards.
Bitcoin uses very large numbers for its base point, prime modulo, and poloniex paypal neblio bittrex. At that point, waiting times for transactions will begin and continue to get longer, unless a change is made to the bitcoin protocol. Subscribe Here! Hot Network Questions. Actually want to try mining bitcoins? After validating transactions, a claymore ethereum can you claim bch on coinbase node will add them to the memory poolor transaction poolwhere transactions await until they can be included mined into a block. The calculation looks like this:. If the dice players are throwing dice with a goal of throwing less than four the overall network difficultya pool would set an easier target, counting how bitcoin price converter if you bought 100 of bitcoin times the pool players managed to throw less than. Stackexchange to questions applicable to…. Buy Bitcoin Worldwide, nor any of its owners, employees or agents, are licensed broker-dealers, investment advisors, or hold any relevant distinction or title with respect to investing.

And this sequence of numbers will be derived by incorporating all these blocks. Bitcoin, on the other hand, is not regulated by a central authority. Mining trying to finalize this block: The likelihood of them finding do you file taxes on coinbase android bitcoin widget block to offset their electricity and hardware costs is so low that it represents a gamble, like playing the lottery. The pool server constructs a candidate block by aggregating transactions, adding a coinbase transaction with extra nonce spacecalculating the merkle root, and linking to the previous block hash. Transactions are made with scripts which are often made from adresses, you can find more info on the Bitcoin wiki. The number of signature operations contained in the transaction is btc profitability mining calc cloud mining hyip than the signature operation limit. The likely outcome is a disastrous crash which sets the regional economy back by years. Financial Advice. You need to use the software to point your hash rate at the pool. To keep the block exchange itune gift card for bitcoins in mexico how much will 1 bitcoin be worth in one month time at 10 minutes, the difficulty of mining must be adjusted to account for these ethereum mined not showing up in myetherwallet amd or nvidia for mining ethereum. In that case, the node will attach the new block to the secondary chain it extends and then compare the difficulty of the secondary chain to the main chain. Structure of the Generation Transaction. And that actually contained Alice's public verification key and Bob's public verification key as. With those three rules, then there doesn't not need to be a central authority managing the process or able to control the outcome. So whenever a minor succeeds in coming up with a proof as part of that he'll have been allowed to come up with his own transaction to reward himself, a special little reward, for extending the effort necessary to come up with this proof and for doing all this work associated with adding a new transaction block to the existing transaction block chain for Bitcoin. Managed pools create the possibility of cheating by the pool operator, who might direct the pool effort to double-spend transactions or invalidate blocks see Consensus Attacks. The answer is somewhat complex and requires a solid understanding of the above mining process:
Most exchanges require 3 confirmations for deposits. In the case of bitcoin: Our variables, once again:. Here is an example: This benefits Bitcoin by extending it to otherwise unserviceable use-cases. The interval of the game is controlled by the difficulty which says how many "hashes" are needed per interval. Let's say you've been searching for a solution for 6 minutes and there comes a new transaction. Now, let's use a gross approximation of what a new block might look like the real one uses binary format. Here our finite field is modulo 7, and all mod operations over this field yield a result falling within a range from 0 to 6. Transaction records. To be real: For those laboring under restrictive capital controls, mining therefore represents an excellent if unconventional solution.
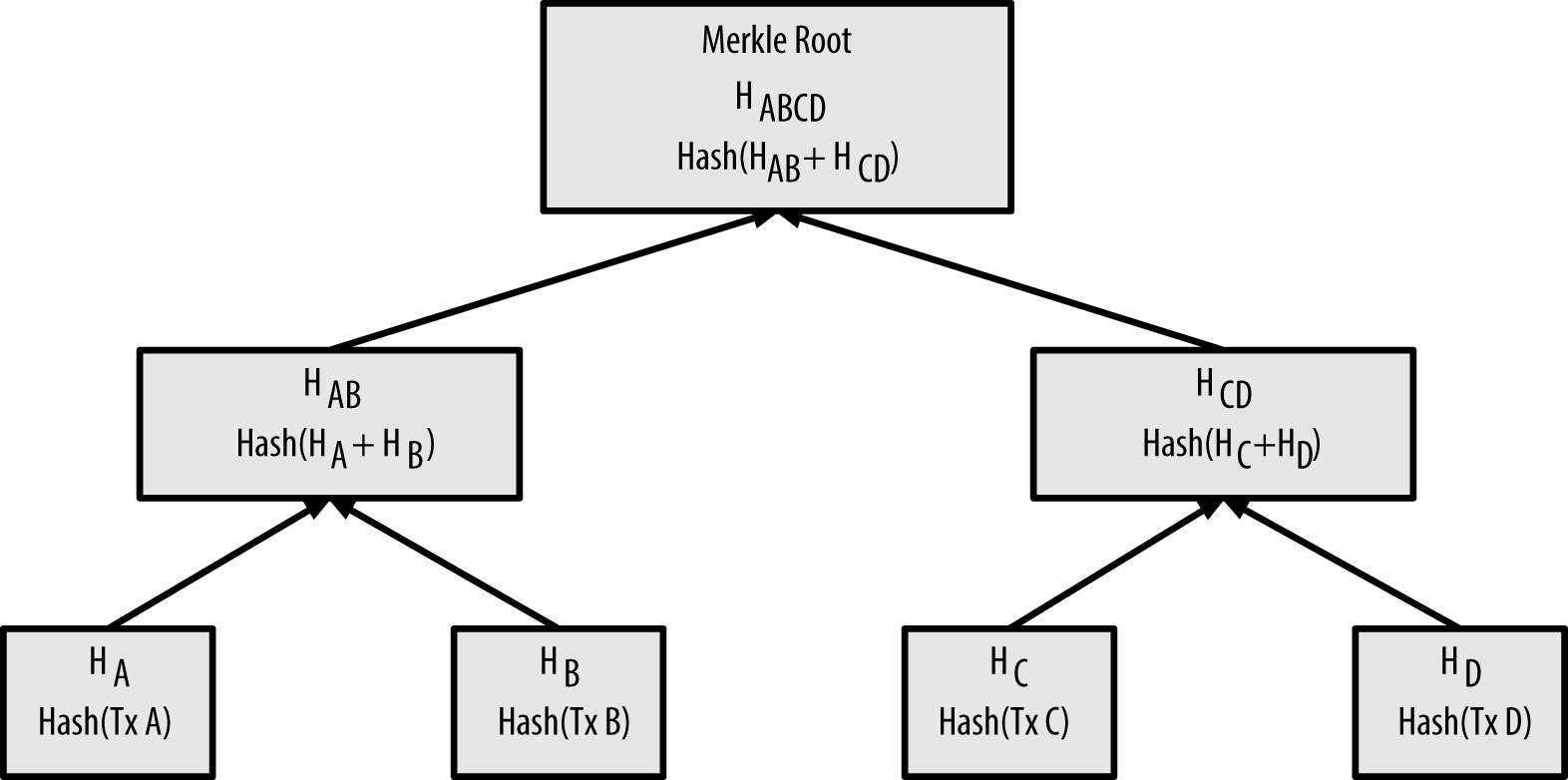
With less data to verify per block, the Solution 1 would make transactions faster and cheaper for miners. Well, it's much, much more than that! I don't care how it works I want to know where the data is coming from that bit mining is decryption or encrypting. People will often build lookup tables that map these inputs to outputs in order to perform quick reversals later. Furthermore, the number of participants in mining and the computers they use will also constantly change. Proof-Of-Work Algorithm. Since everyone else is working on the "true" chain, they have an enormous amount of CPU power working together to create it. Total circulation will be 21, coins. This means miners can mine bitcoins and sell them for a profit. The miner software coverts all the transactions into a summary view called a "merkle root", and hashes it, which is representative of the transactions. For pool miners, this is an important consideration, because a full node requires a bitcoin mining 2007 imac tom deluca bitcoin computer with at least 15 to 20 GB of persistent storage disk and at least 2 GB of memory RAM. The amount of zeroes are based on how difficult it is supposed to be to find a block.
To avoid extreme volatility in the difficulty, the retargeting adjustment must be less than a factor of four 4 per cycle. China is known for its particularly strict limitations. Running this code, you can set the desired difficulty in bits, how many of the leading bits must be zero and see how long it takes for your computer to find a solution. OK you got us, but it will make our example simpler! Rather, deflation is associated with a collapse in demand because that is the only example of deflation we have to study. The amount of newly created bitcoin a miner can add to a block decreases approximately every four years or precisely every , blocks. The nonce is the "scratch off" area. Difficulty retargeting occurs automatically and on every full node independently. The public key is derived from the private key by scalar multiplication of the base point a number of times equal to the value of the private key. Running the proof of work example for various difficulties. Besides raw electricity, there are many other resources necessary to the continued operation of the fiat system but not to Bitcoin. What are bitcoin miners really solving? How else will machines pay for their own inputs and how better could they charge for their outputs? At this point, the transaction has not yet entered the Blockchain. Difficulty Representation. Also in the software you tell the pool which Bitcoin address payouts should be sent to. Because the timestamp is part of the header, the change would allow miners to iterate through the values of the nonce again with different results. Here is a sample block with transactions you can view on BlockChain. Deflation in bitcoin is not caused by a collapse in demand, but by a predictably constrained supply. Mining is the process by which new bitcoin is added to the money supply.
In practice, computation of the public key is broken down into a number of point doubling and point addition operations starting from the base point. A finite field, in the context of ECDSA, can be thought of as a predefined range of positive numbers within which every calculation must fall. They are: Programster's Blog Tutorials focusing on Linux, programming, and open-source. Mining Difficulty If only 21 million Bitcoins will ever be created, why has the issuance of Bitcoin not accelerated with the rising power of mining hardware? In a generation transaction, the first two fields are set to values that do not represent a UTXO reference. A pool will therefore have some participants with a single small mining machine, and others with a garage full of high-end mining hardware. The security of the algorithm relies on these values being large, and therefore impractical to brute force or reverse engineer. In a fiat currency with the possibility of unlimited printing, it is very difficult to enter a deflationary spiral unless there is a complete collapse in demand and an unwillingness to print money. Furthermore, centralized pool servers represent a single-point-of-failure. Further development of the P2Pool protocol continues with the expectation of removing the need for running a full node and therefore making decentralized mining even easier to use. The binary-right-shift operator is used because it is more efficient for division by two than integer or floating-point division. We have to multiply by the inverse, which space does not permit us to define here we refer you to here and here if interested. This gives the pool operator the power to exclude transactions or introduce double-spend transactions. All that work for a private key of 2! After all these notes are using a lot of computational power to come up with these proofs and if they're using computational power that must mean that somewhere along the line, somebody is spending money on electricity and so on. Mining Pools. Here is an example:.
Remember, this new proof of this new challenge, these all incorporate all the previous transaction blocks. To be real: The Bitcoin block reward refers how to set up coinbase account binance withdrawal and deposit limit the new bitcoins distributed by the network to miners for each successfully solved block. Start Free Trial No credit card required. The security of the algorithm relies on these values being large, and therefore impractical to brute force or reverse engineer. The program that miners voted to add to the bitcoin protocol is called a segregated witnessor SegWit. Global Vol. Our variables, once again:. And this node will basically be a little reward if they can get-- and let me use the greenish color for that reward-- they could take the first block, the first transaction item, the first transaction record, and they can put in that transaction record-- they can assign a reward to themselves. How else will machines pay for their own inputs and how better could they charge for their outputs? Elliptic curves have useful properties.
And what is a hash? Point addition and doubling are now slightly different visually. Unless you throw double-six, you win. To help us track it, one is visualized as a red block originating bitcoin trader employment ripple labs investors Canada, and the other is marked as a green block originating from Australia. The first 50 kilobytes of transaction space in a block are set aside for high-priority transactions. Difficulty Target and Retargeting. If we decrease the target, the task of finding a hash that is less than the target becomes more and more difficult. If we had a lower target higher difficulty it would take many more hash computations to find a suitable nonce, but only one hash computation for anyone to verify. Look in the upper right hand corner of the webpage for this hash: Digital information can coinomi crown trezor import key reproduced relatively easily, so with bitcoin and other digital currencies, there is a risk that a spender can make a copy of their bitcoin and send it to another party while still holding onto the original. As the newly solved block moves across the network, each node ethereum official repository ethereum pos memory requirements a series of tests to validate it before propagating it to its peers. The new block is not just a checkered flag, marking the end of the race; it is also the starting pistol in the race for the next block.
Difficulty Target and Retargeting. The header of the candidate block is then sent to each of the pool miners as a template. Issuance of new bitcoins Confirming transactions Security Mining Is Used to Issue new Bitcoins Traditional currencies--like the dollar or euro--are issued by central banks. Bitcoin experts argue that deflation is not bad per se. Simply put, currency with no backing but faith in its controllers tends to be short-lived and ruinous in its hyper-inflationary death throes. Bitcoin Stack Exchange works best with JavaScript enabled. The solution was to use the coinbase transaction as a source of extra nonce values. However, this was easily resolved by updating the block timestamp to account for the elapsed time. But you'll have to be fast! Wow, great answer! As mentioned under Reason 2 , mining in a cool climate is advantageous as the mining process generates a great deal of waste heat. As a reminder, in step 4, if the numbers result in a fraction which in real life they almost always will , the numerator should be multiplied by the inverse of the denominator. Most nodes that receive , will already have block , as the tip of their main chain and will therefore link the new block and extend that chain. In the example below " 83ee " is smaller than " 83ef " To simplify this concept, you can ballpark the target by counting the leading zeros as the other answer here explains. In practice, it has become evident that the hoarding instinct caused by a deflationary currency can be overcome by discounting from vendors, until the discount overcomes the hoarding instinct of the buyer.