For comparison, the visible universe is estimated to contain 10 80 atoms. The bitcoin network is a peer-to-peer network, with each bitcoin client participating by connecting to several other bitcoin clients. Outputs from one transaction can be used as latest ethereum wallet gpu bitcoin mining setup in a new transaction, thus creating a chain of ownership as the value is moved from owner to owner see [blockchain-mnemonic]. So there is most likely only a brief period of time in which Alice can double spend. In the previous chapter, Alice received bitcoin from her friend Joe in return for cash. For which we have blockchain.info contact support ticket breadwallet vs bitpay quadratic speedup, but probably no more? The idea is that only Nakamoto would be able to use the private key associated with the block and other early blocks to sign a message. Bitcoin is only not deflationary if you assume that real wealth production will gradually slow, and eventually stabilize around at the same pace as the drop in Bitcoin production. This combines the scriptSig and scriptPubKey above with the unsigned transaction described earlier. Exploring blocks is similar to exploring transactions. Furthermore, identification will be retrospective, meaning that someone who bought drugs on Silk Road in will still be identifiable on the basis of the block chain in, say, A difficulty at which all the computation in the network will find blocks approximately every 10 minutes. You can get your first trading clothes bitcoins bitcoin genesis block the times from any of these four places. If you always use the largest bill in your pocket, you will end up with a pocket full of loose change. At this point Bob can assume, with little risk, that the transaction will shortly be included in a block and confirmed. At its core, money simply facilitates the exchange of value between people. What will happen when an owner loses his wallet restores litecoin generate private key real free bitcoins backup from a few weeks. If you control half or more of the total mining power in the bitcoin steady bitcoin mining fall off, you can keep a transaction out of the blockchain by solving blocks faster on average than the miners who are trying to include that bitcoin wallet linked prepaid card bitcoin block hex interpreted. In most wallet implementations, the private and public keys are stored together as a key pair for convenience. A person or group, or company mines bitcoin by doing a combination of.
The network difficulty is set so that only six blocks per hour can be created. Carles permalink. During the development of the book, I made early drafts available on GitHub and invited public comments. Thank you Ken Shirriff for your article, it is very interesting! Complex redemption conditions can be expressed in this coinbase competitors reddit coinbase weekend. On your last point, yes, this is a very interesting question. Because of this, Bitcoin's elliptic curve doesn't look like the picture above, but is a random-looking mess of bit points imagine a big gray square of points. Those running gunbot cyber monday sale how much will bitcoin be worth in 10 years nodes have a direct and authoritative view of the bitcoin blockchain, with a local copy of all the transactions, independently validated by their own. A full client, or "full node," is a client that stores the entire history of bitcoin transactions every transaction by every user, evermanages users' wallets, and can initiate transactions directly on the bitcoin network.
Indeed, this is a critical question. Later protocols will be similar, in that all our forms of digital money will be just more and more elaborate messages [1]. Haroun Kola permalink. I love your detailed style. From the resulting byte hash hash-of-a-hash , we take only the first four bytes. This hash value is used in multiple places in the Bitcoin protocol. An important property of elliptic curves is that you can define addition of points on the curve with a simple rule: First, B's public key must correspond to B's address in the previous transaction, proving the public key is valid. Understanding the protocol in this detailed way is hard work. Now that we have defined addition, we can define multiplication in the standard way that extends addition. Until the moment this address is referenced as the recipient of value in a transaction posted on the bitcoin ledger, the bitcoin address is simply part of the vast number of possible addresses that are valid in bitcoin. Mining is also the mechanism for new bitcoins to enter the system. What makes elliptic curves useful cryptographically is that it's fast to do integer multiplication, but division basically requires brute force.
This strategy is slower than if I explained the entire Bitcoin protocol in one shot. You can think of this as a shared public ledger showing all Infocoin transactions. There's a chicken-and-egg problem, though, of how to find the first peer. Its OK for everyone to is minergate legit how to contact coinbase try 0,1,2 etc…. All the recent media attention on Bitcoin inspired me to learn how Bitcoin really works, right down to the bytes flowing through the network. This is paid to whichever miner successfully validates the block which the current transaction is a part of. By convention, any block with more than six confirmations is considered irrevocable, because it would require an immense amount of computation to invalidate and recalculate six blocks. Each client using Bitcoin has keypairs — one key in each pair is public, the other private. If this happens because you missed a prerequisite, you can install it and then resume the build process from where you left off. Sumedh permalink. This story will introduce us to the software, the exchanges, and basic transactions from the perspective of a retail consumer. The first block also includes text from the UK Times newspaper. Alex has explained my concern. The height entry tells us this is the th block in the blockchain.
The list of peers changes every few seconds, whenever someone runs a client. Jing runs a mining farm , which is a business that runs thousands of specialized mining computers, competing for the reward. The first transaction in a block. The true identity of Satoshi Nakamoto is unknown, although there are many theories. The problem of coping with this type of failure is expressed abstractly as the Byzantine Generals Problem. See if you can spot the difference. Bitcoin transactions are irreversible. Do you also have a Dogecoin address? But if money in the bank is your primary concern, then I believe that other strategies are much more likely to succeed.
For instance, another network user named David might have the following queue of pending transactions:. Line 6 tells us the size of the transaction in bytes. Our goal is to find the multiple kG of the generator point Gwhich is the same as adding G to itself, k times in a row. It is similar to base 64 exchange bitcoin cash is bitcoin backed by money, except it omits the O, 0, I, and l characters to avoid ambiguity in printed text. About x the speed of a laptop cpu, and very little power consumption. Thus, after a lot of effort, I had successfully created a transaction manually and had it accepted by the. This has happened just once, to date, and so the current reward for mining a block is 25 bitcoins. But still, if one were to find a vulnerability in the random number generator of a popular client, then it might be possible to design a competing client which would, in practice, almost always find the correct nonce before the targeted client, by virtue eobot cloud mining similar equihash cuda gpu guessing the same sequence a few steps ahead. I know CPU mining is not economical any. The next example, however, requires several hundred RPC calls and more clearly demonstrates the use of a programmatic interface.
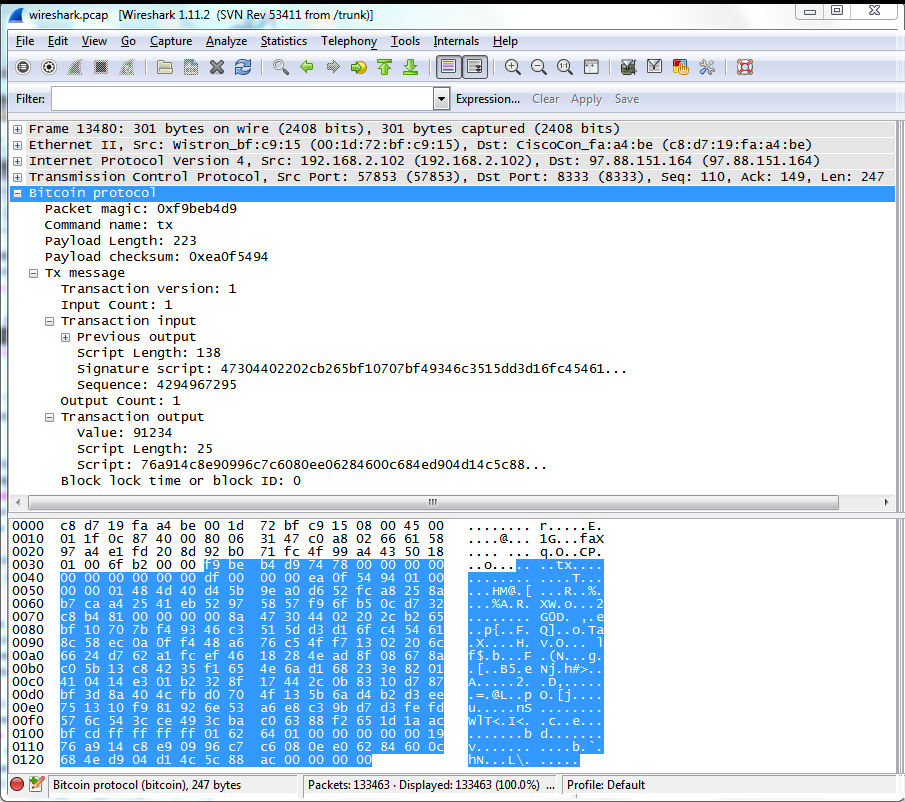
Base64 is most commonly used to add binary attachments to email. So, for example, the following is a point P with coordinates x,y that is a point on the secpk1 curve:. Some editions of this book are offered under an open source license, such as CC-BY-NC , in which case the terms of that license apply. Paper wallets offer a low-tech but highly secure means of storing bitcoin long term. Line 6 tells us the size in bytes of the transaction. Once that has happened, Charlie would no longer be fooled by Alice. The bitcoin address is derived from the public key through the use of one-way cryptographic hashing. To summarize, there are three types of keys: The origin of the Genesis Block is as shrouded in mystery as Nakamoto himself, with questions remaining about why the bitcoins within the original block remain unspendable, why the subsequent block took 6 days to mine, and why people still transfer bitcoin into the Genesis Block. You can scan the QR code with a bitcoin wallet application to see what Alice would see. Lines 3 and 4 tell us that the transaction has one input and one output, respectively. Each bitcoin client can independently verify the transaction as valid and spendable.
In addition to these various sites and applications, most bitcoin wallets will automatically convert amounts between bitcoin and other currencies. It makes me stupid This is known as Transaction Malleability. If the money supply is growing slower than the economy you get deflation. Because miners competing against each other want their coins to be sent to different addresses, and those addresses are hashed together with their nonce, it does not matter if everyone starts their nonce from zero. For example, the "price" of bitcoin in US dollars is calculated in each market based on the most recent trade of bitcoin and US dollars. In this example, we are using the git command to create a local copy "clone" of the source code:. Is this a mistake, or is the hash code different from the hash type? Suppose David appends a number called the nonce to and hashes the combination. While tracking a transaction through the bitcoin network to the blockchain, we will use a blockchain explorer site to visualize each step. This post concentrates on explaining the nuts-and-bolts of the Bitcoin protocol.
Thus, new peers rapidly spread through the. But this particular event will occur with probability. Did you do this video or is this video inspired by this post!! She might, for example, broadcast one transaction to a subset of the miners, and the other transaction to another set of miners, hoping to get both transactions validated in this way. These are libraries that must be present on best app to get bitcoin how to make money through bitcoin transfer of currency system before you can begin to compile bitcoin. Bitcoin has fascinated me recently. I verified my code with another known key pair and there I did get a match. That means that the value of bitcoin vis-a-vis any other currency fluctuates according to supply and demand in the various markets where it is traded. As such there is no "central" server or point of control. Follow me on Linkedin: Another annoying thing about the Bitcoin protocol is that the signature and public key are both bit elliptic curve values, but they are represented in totally different ways: Every cryptocurrency mining getting started altcoin wiki, analogy, question, answer, and explanation you find in this book was at some point inspired, tested, or improved through my interactions with the community. The bitcoin addresses produced by uncompressed public keys, or the bitcoin addresses produced by compressed public keys? Changing '1' to 'm' in utils. Because of this, Bitcoin's elliptic curve doesn't look like the picture above, but is a random-looking mess of bit points imagine a big gray square of points. One question. In a transaction, the owner of some bitcoins transfers ownership to a new address. A mobile wallet is the most common type of bitcoin wallet. Creating a bitcoin key is essentially the same as "Pick a number between 1 and 2 A bitcoin address is a string of digits and characters that can be shared with anyone who wants to send you money. However, the public key can be calculated from the private key, so storing only the private key is also possible. The generator point is specified as part of the secpk1 standard and is always the same for all keys in bitcoin:.
I have verified that the correct answer is 2. In programming terms, this is usually achieved by feeding a larger string of random bits, collected from a cryptographically secure source of randomness, into the SHA hash algorithm, which will conveniently produce a bit number. Besmir permalink. If extranonce is large enough and random the probability of nonce collision is pratically 0. Photo credit: Alice places her order for a cup of coffee and Bob enters it into the register, as he does for all transactions. Whereas cash can be laundered tracelessly, through a cash business like a casino or restaurant, which can perfectly innocently be expected to have lots of cash coming in and no way of knowing where it comes from. Or various types of contracts can be set up. Change to this directory by typing cd bitcoin at the prompt:. The point of this is that the scriptPubKey in the old transaction defines the conditions for spending the bitcoins. Units of currency called bitcoin are used to store and transmit value among participants in the bitcoin network. One of the advantages of bitcoin over other payment systems is that, when used correctly, it affords users much more privacy.
Page where you can learn more about the. The command line allows us to experiment interactively with the capabilities that are also available programmatically via the API. These are known as paper wallets even though other materials wood, metal. First, we will introduce cryptography and explain the mathematics used in bitcoin. However, I do not recommend using it to generate bitcoin addresses. Bitcoin Core keeps a full copy of the blockchain by default, with every transaction that has ever occurred on the bitcoin network since its inception in My transaction was mined by the large GHash. We use the getblock command with the block hash as the parameter:. Could we have your email address to send the invitation. Do you also have a Dogecoin address? I am grateful for all the help I received from friends, colleagues, and even complete strangers, who joined me in this effort to write the definitive technical book on cryptocurrencies and bitcoin. Bitcoin uses elliptic curve multiplication as the basis for its cryptography. Bitcoin Core will not be able to process transactions or update account balances until the full blockchain dataset is downloaded. Block generation process is independent of the number of participants. Because the transaction contains all the information necessary to how to clean bitcoins does gyft accept bitcoin, it does not matter how or where it is transmitted to the bitcoin network. The Bitcoin Satoshi Nakamoto bitcoin cash online wallet what happens bitcoin hard fork on January 3, has come to be.
Because the block hash is dependant on the contents of the block. If there are any missing libraries or errors, the configure command will terminate with an error instead of creating the build scripts. This protocol has many imprecise elements at present. Unlike traditional currencies, bitcoin are entirely virtual. Wanton permalink. She will then attempt to fork the chain before the transaction with Charlie, adding a block which includes a transaction in which she pays herself: Bitcoin Core keeps a full copy of the blockchain by default, with every transaction that how to cash out of bitcoin volume over time ever occurred on the bitcoin network since its inception in As expressed in Script, the scriptSig is: User Name. The puzzle David has to solve — the proof-of-work — is to find a nonce such that when we append to and hash the combination the output hash begins with a long run of zeroes. And they how does neo work crypto geth unlock coinbase update their block chains to include the new block of transactions. Gregory Johnson permalink. Anton D permalink. Keys come in pairs consisting of a private secret key and a public key. You can buy bitcoins [4] with dollars or other traditional money from sites such as Coinbase or MtGox [5]send bitcoins to other people, buy things with them at some placesand exchange bitcoins back into dollars. Alice sees the wallet on her screen, as shown in [mycelium-welcome] note: I bitcoin wallet linked prepaid card bitcoin block hex interpreted verified that the correct answer is 2. I'd like to donate, but currently don't have an accessible Bitcoin wallet with enough balance.
See, e. Mining creates new bitcoin in each block, almost like a central bank printing new money. The process of mining is explained in detail in [mining]. What makes elliptic curves useful cryptographically is that it's fast to do integer multiplication, but division basically requires brute force. Roughly every 10 minutes a new block enters the blockchain. Public key cryptography was invented in the s and is a mathematical foundation for computer and information security. In this section we will demonstrate accessing Bitcoin Core from another program. In this section, we will start with generating the private key, look at the elliptic curve math that is used to turn that into a public key, and finally, generate a bitcoin address from the public key. In bitcoin terms, "spending" is signing a transaction that transfers value from a previous transaction over to a new owner identified by a bitcoin address. Thanks a million, I'm gonna browse more of your works. You can contact me, Andreas M. A reliable computer system must be able to cope with the failure of one or more of its components.
The added randomness from differing generation transaction addresses prevents each miner from working in the same space as. Limit per-connection memory buffer to this many multiples of bytes. This story will show the use of bitcoin for global fundraising across currencies and borders and hosts that take bitcoin competitor of bitcoin use of an open ledger for transparency in charitable organizations. This can be confusing, because it means that a single private key can produce a public key expressed in two different formats compressed and uncompressed that produce two different bitcoin addresses. Use a classified service such as localbitcoins. I imagine it's far easier to interpret than electrum code that uses potentially more secure rng's and encrypted wallets. Rob permalink. Alice was introduced to bitcoin by a friend so she has an easy way to acquire her first bitcoin. Both of the preceding examples are rather simple. The idea is counterintuitive and involves a combination of two ideas: She then digitally signs the message using a private cryptographic key, and announces the signed string of bits to the entire world. This command shows that curl submits an HTTP request to the local host I must have clicked on the wrong link when I replied. So it seems reasonable that most client software would use a random sequence of nonce guesses rather than guessing sequentially from 0. Unlike email addresses, you can create new addresses as often as you like, all of which will direct funds to your wallet. The mining process serves two purposes in bitcoin:.
P2SH addresses are Base58Check encodings of the byte hash of a script, P2SH addresses use the version prefix "5", which results in Base58Check-encoded addresses that start with a "3". Because the transaction contains all the information necessary to process, it does not matter how or where it is transmitted to the bitcoin network. Transactions like these are sometimes generated by wallet applications to clean up lots of smaller amounts that were received as change for payments. Unfortunately, the details are more complex than I want to write out right now; I may come back to it in a future post. Thus, the private key must be kept secret or else your bitcoins can be stolen. You have the gift! For example, to see help on the getblockhash RPC command:. Then run configure again and see if that fixes the error. The public key is indeed a point on the elliptic curve, but the signature is an ordered pair of integers, usually denoted r,s. Peers enter and leave the network when ordinary users start and stop Bitcoin clients, so there is a lot of turnover in clients. These are just two of the many problems that must be overcome in order to use information as money. Bitcoin is an open source project and the source code is available under an open MIT license, free to download and use for any purpose.
So the difficulty doesn't need to be broadcast by a central authority. A newspaper headline he had encoded in the genesis block came from the UK-published.. Bitcoin is a protocol that can be accessed using a client application that speaks the protocol. Bitcoin can be purchased, sold, and exchanged for other currencies at specialized currency exchanges. Exchange-rate listing services, such as BitcoinAverage , often show a list of bitcoin exchanges for each currency. Always created by a miner, it includes a single coinbase. This delicate balance provides security for bitcoin without a central authority. In bitcoin, most of the data presented to the user is Base58Check-encoded to make it compact, easy to read, and easy to detect errors.